Multi-Tenant Security Management with Microsoft Sentinel and Microsoft Defender XDR
In today's rapidly evolving digital landscape, managing security across multiple tenants has become a paramount challenge for large enterprises. As organizations expand and diversify, they increasingly rely on multi-tenant environments to streamline operations and enhance efficiency. However, this complexity introduces significant security risks, necessitating robust solutions that can adapt to the intricate needs of multi-tenant management.
Enter Microsoft Sentinel and Microsoft Defender XDR—two cutting-edge tools that are redefining the standards for security operations in complex, multi-tenant architectures.
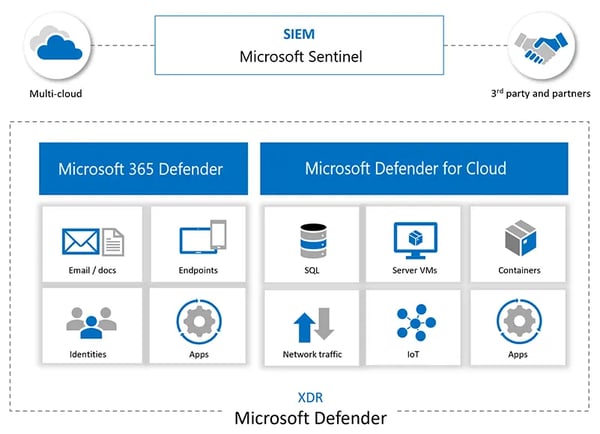
This blog delves into how Microsoft Sentinel and Microsoft Defender XDR empower organizations to enhance their security operations, offering a deep dive into their capabilities, architectural considerations, and the tangible benefits they bring to multi-tenant management.
Microsoft Sentinel, a cloud-native SIEM (Security Information and Event Management) system, and Microsoft Defender XDR (Extended Detection and Response) provide a full suite of capabilities designed for large enterprise environments with multi-tenant instances.
These capabilities ensure advanced security monitoring, threat detection, and incident response all across an organization's digital estate.
Microsoft Sentinel capabilities:
- Cloud-Native SIEM Solution: It's a cloud-native SIEM solution designed to help organizations reduce the massive requirement for setting up and managing security operations infrastructures.
- AI and Machine Learning: By leveraging AI and machine learning to analyze the humongous amounts of data created throughout the organization, Sentinel does the reduction of false positives and brings sophisticated threats to the surface.
- Advanced Threat Detection and Response: In this sense, Sentinel has the prowess to sense, respond, and automate incidents, providing proactive hunting of potential threats so that the security team can respond with agility to avert potential security threats.
- Security Built into the Stack: Microsoft invests heavily in security, drawing upon the expertise of thousands of security professionals. Microsoft products are engineered with robust security features embedded throughout to ensure compliance with industry standards.
Microsoft Defender XDR functionalities:
- Extended Detection and Response: Defender XDR ensures comprehensive security coverage of endpoints, hybrid identities, emails, collaboration tools, and cloud apps, all from one single unified security posture.
- Incident-level Visibility: A high level of detailed visibility across the cyber attack chain could increase the coordination and possibly the speed of a sophisticated cyber attack.
- Unified security and access management: Defender XDR consolidates security and access management, with unity to manage security across platforms and clouds.
- Cross-Threat Hunting and Threat Analytics: Stitch threat signals from various products together and determine full scope and impact of the attack. This will also be beneficial in realizing how the threat comes into the environment, the attacked surface, and its present impact on the organization.
Architectural considerations towards the enterprises running multi-tenant instances:
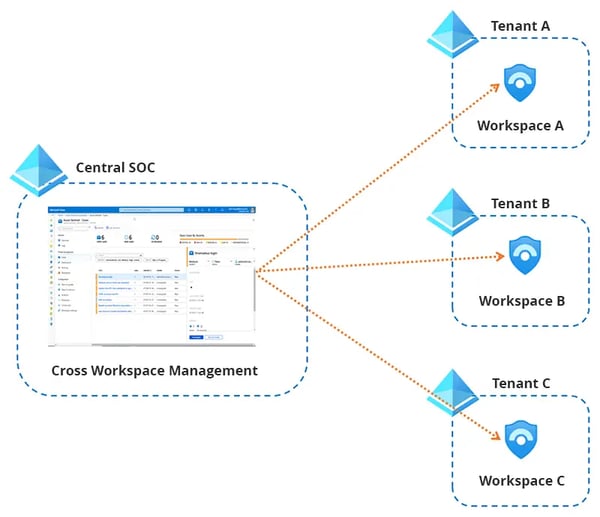
The enterprise running multi-tenant instances hosted on Microsoft Sentinel would base architectural considerations for a data ingestion and monitoring framework towards it on the following steps:
- Workspace selection and setup: Start with care in choosing a Log Analytics workspace as the first and primary step when onboarding to Microsoft Sentinel. This may be the need in order to extend the workspace to be able to ask queries and perform analysis across more than one workspace and tenant in a multi-tenant environment.
- Multi-Workspace Incident View and Central Incident Management: Microsoft Sentinel gives a cross-workspace multi-incident view and serves as a central point for incident management. It is possible to monitor and manage incidents centrally regardless of their workspace location. This aspect allows one to manage or further drill down incident details to their originating workspace context.
- Querying across workspaces: One can have queries running across several workspaces, thus searching and correlating data in one single query. This could be achieved using the `workspace()` expression and the `union` operator so as to span the queries across the tables of different workspaces and thus contribute to the enhancement of the ability to monitor and analyze data at large scale.
- Cross-workspace analytics rules: Scheduled analytics rules can span cross-workspace queries, for the purpose of supporting centralized SOC operations and extending capabilities across tenants. This configuration supports up to 20 workspaces per query, with a recommendation for optimal performance that this be no more than five.
- Multi-Workspace and Tenant Setup: If multi-workspace architecture forms part of your deployment strategy, then set up should be critical in your deployment. It manages and monitors the architecture by querying and analyzing data across workspaces and tenants while centrally managing several workspaces in one or more Azure tenants.
Architecture recommendations for Managing Multiple Tenants:
- Multi-tenant deployment architecture: The multi-tenancy architecture for deploying Microsoft Sentinel and Defender XDR in an environment that will cater to the isolation and segregation of resources for each of the tenants with the use of Microsoft Entra ID, which will give seamless authentication and authorization of users across tenants.
- Data Ingestion and Integration: Ingest security data, logs, and telemetry from various sources across all managed tenants using the various connectors available in Microsoft Sentinel, data connectors, and custom data ingestion facilities. Integrate with Microsoft Defender XDR and other Microsoft security solutions to enrich security analytics and correlate the events across different layers of the technology stack.
- Centralized Security Operations Center (SOC): Implement a Unified Security Operations Center (SOC) with Microsoft Sentinel Unified Dashboards, Workspaces, and Visualization tools, facilitating visibility over the monitoring of security events and incidents from various points of the managed tenants. Customize dashboards and reports to present the security metrics, trends, and compliance status of the tenancy.
- Automated Incident Response and Remedization: Implement automated incident response and remedization workflows within Microsoft Sentinel that will allow response actions like endpoint isolation, blocking malicious IP addresses, quarantining suspicious files, among others, across all managed tenants. Ability to be integrated with 3rd-party security tools and custom workflows through Azure Functions, Logic Apps, or ease of integration with PowerShell scripting extensions.
- Continuous Monitoring and Optimization: Continually monitor and optimize the performance and efficacy of managed security operations. Periodically review and assess the security policies, configurations, and workflows in order to identify opportunities for improvement and maintain compliance to dynamic business and regulatory requirements.
Some challenges that Quzara Cybertorch has identified and overcome leveraging Microsoft Sentinel & Defender XDR:
- Securing the Federal Agencies:
Challenge: They have very tight compliances and security standards set on the federal bodies since they have very sensitive data being handled.
Solution: Microsoft Sentinel and Defender XDR grant them centrally automated compliance enforcement tools for security management. Agile in enhanced security visibility and response mechanisms for better security and compliance.
Benefit: Strengthened resilience against sophisticated cyber threats through continuous monitoring, real-time threat detection, and swift incident response, ensuring uninterrupted operations and safeguarding critical assets within the Defense Industrial Base ecosystem. - Defense Industrial Base (DIB) Protection:
Challenge: Supply chain attacks and espionage attacks represent some of the highest orders of cyber threats that the U.S. DIB sector may be subjected to.
Solution: Microsoft Sentinel and Defender XDR helps DIB organizations implement new network-wide advanced threat detection and response capabilities.
Benefit: A collective security framework will provide a coherent mechanism for the protection of the relevant data and enhancing the resilience of the supply chain as a whole.
Summary: Microsoft Sentinel and Defender XDR are robust, scalable, and cost-effective solutions appropriate for even large enterprises managing multi-tenant instances. Their AI capabilities, robust integrations, and native cloud architecture outdo other traditional SIEM systems, and they are preferably used within a security operations center of the modern age.
At Quzara, we utilize our Cybertorch solution to maintain robust security within our multi-tenant architecture, integrating Microsoft Sentinel and Defender XDR for efficient threat detection. This setup enables us to effectively manage and safeguard our diverse environments, ensuring a strong security posture across all tenants. By choosing Quzara Cybertorch, you'll gain the benefit of our proven expertise in protecting complex multi-tenant systems with cutting-edge technology. Click below to learn how we can help secure your multi-tenant environment.



