If your organization is involved in the world of Government Information Technology (IT), chances are you've come across the term "FedRAMP" before. But what exactly is FedRAMP, and why is it so important?
In this blog post, we'll take a deep dive into all things FedRAMP – from understanding its importance to exploring the process of pursuing an agency authorization. So, whether you're a Cloud Service Provider (CSP) looking to obtain agency authorization or an agency seeking guidance on achieving compliance with FedRAMP requirements, this blog will serve as your comprehensive guide through the complexities of FedRAMP. Let's get started!
- What is FedRAMP?
- Why is FedRAMP so Important?
- What are the Roles and Responsibilities of FedRAMP, CSPs, and Agencies?
- What is the FedRAMP Authorization Process?
- How to Prepare for Authorization?
- What are the Phases of the Authorization Process?
- What are FedRAMP Compliance Requirements?
- How Quzara Can Help?
What is FedRAMP?
FedRAMP is a government-wide initiative that sets the standard for cloud security for federal agencies and CSPs that support them. It was established to streamline and improve the authorization process for CSPs seeking to work with government entities. FedRAMP also helps build trust among potential customers by showcasing your organization’s commitment to robust security measures.
The program provides a consistent framework for assessing and authorizing CSP offerings based on NIST 800-53 Revision 5 controls. It enables CSPs to undergo an assessment by an accredited third-party assessment organization (3PAO) to demonstrate compliance with these controls.
Why is FedRAMP so Important?
In today's digital age, data security is of utmost importance for both government agencies and commercial organizations. This is where FedRAMP comes into play. FedRAMP provides a standardized approach to architecture, engineering, security assessment, authorization, and continuous monitoring for CSPs.
One of the key reasons why FedRAMP is so important is because it ensures that CSPs meet stringent security requirements set forth by the federal government. By adhering to these standards, CSPs can gain the trust of government agencies and demonstrate their commitment to protecting sensitive information.
Furthermore, FedRAMP helps streamline the procurement process for federal agencies by providing a marketplace where they can easily find authorized cloud services and leverage Authority-To-Operate (ATO) packages issued by other agencies or the Joint Authorization Board (JAB). This not only saves time, but also ensures that agencies are selecting CSPs that have been thoroughly vetted and approved. In return, obtaining FedRAMP authorization opens the door to opportunities for CSPs to work with various federal agencies. Many government organizations require vendors to have a FedRAMP Authorization to ensure compliance with data protection regulations.
Furthermore, through its continuous monitoring program, FedRAMP ensures ongoing compliance with security controls even after an initial authorization has been granted. This proactive approach helps identify any potential vulnerabilities or risks and allows for timely remediation actions.
The importance of FedRAMP cannot be overstated in today's evolving cybersecurity landscape. It provides a framework for ensuring the confidentiality, integrity, and availability of sensitive data and best practices, while enabling collaboration between government agencies and trusted cloud service providers.
What are the Roles and Responsibilities for FedRAMP, CSPs, and Agencies?
FedRAMP involves the collaboration of various entities to ensure the security of cloud services. Each party has specific roles and responsibilities that contribute to the program's overall success.
- Federal Risk and Authorization Management Program (FedRAMP):As the governing body, FedRAMP establishes policies, procedures, and guidelines for cloud service providers (CSPs) seeking authorization. They also manage the continuous monitoring process.
- Cloud Service Providers (CSPs):CSPs are responsible for implementing robust security controls within their systems. They must undergo a rigorous assessment to demonstrate compliance with FedRAMP requirements
- Agencies: Agencies play a crucial role in selecting and using secure cloud services. They evaluate CSP offerings based on their specific needs while ensuring compliance with FedRAMP standards.
- FedRAMP Program Management Office (PMO):The FedRAMP PMO resides within GSA and supports agencies and cloud service providers through the FedRAMP authorization process and maintains a secure repository of FedRAMP authorizations to enable reuse of security packages. The PMO acts as a central governing body for FedRAMP and provides guidance, oversight, and support throughout the entire lifecycle of agency authorizations. They offer training programs, webinars, and workshops to educate stakeholders on best practices for achieving compliance. The PMO can be reached by emailing info@fedramp.gov
- Joint Authorization Board (JAB): The JAB consists of Chief Information Officer representatives from major federal agencies who review high-impact systems' authorizations. Their approval signifies that a CSP meets stringent security requirements.
- Third-Party Assessment Organizations (3PAOs): 3PAOs conduct independent assessments of CSPs' systems to determine compliance with FedRAMP controls; they provide valuable expertise in evaluating systems and assist in preparing packages for submission.
- Cloud Service Providers - System Owner: The system owner is responsible for managing and operating their cloud system in accordance with established security controls outlined by FedRAMP.
By understanding these roles and responsibilities, all parties involved can collaborate effectively towards achieving secure cloud environments that meet federal standards.
What is the FedRAMP Authorization Process?
The Authorization Process is a crucial step in obtaining FedRAMP Agency Authorization. Once a Cloud Service Provider (CSP) has completed their documentation and prepared their system for assessment, they can move forward with the authorization process.
During this phase, the CSP will submit their System Security Plan (SSP) to the agency sponsor or Joint Authorization Board (JAB) (if selected). The SSP outlines how the CSP implements security controls based on NIST 800-53 Revision 5 guidelines. Additional guidelines on top of the NIST 800-53 Revision 5 maybe be required to be followed on an agency-by-agency basis.
Once submitted, the agency sponsor or JAB will review the SSP and conduct an initial assessment of the system. This may include interviews and document reviews to ensure compliance with FedRAMP requirements.
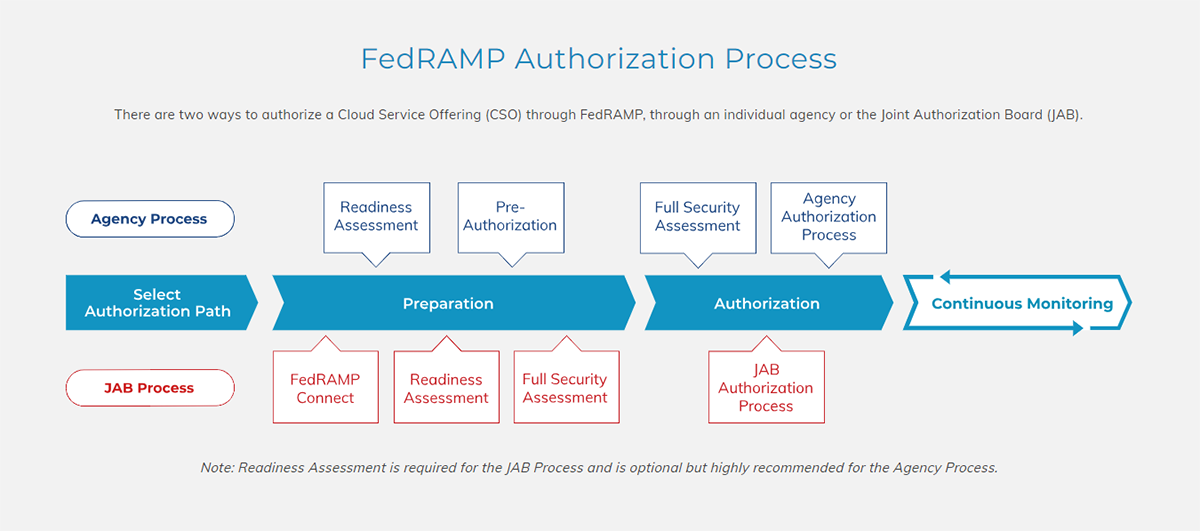
If any issues are identified during this assessment, the CSP will need to address them before moving forward. Once all issues are resolved, the agency sponsor or JAB will grant an Authority to Operate (ATO).
Throughout this process, open communication between all parties involved is key. It's essential for both CSPs and agencies to collaborate effectively to achieve successful authorization within a reasonable timeframe.
However, it's important to note that achieving FedRAMP compliance is not a one-time event but rather an ongoing commitment. Once authorized, CSPs must continually monitor their system’s performance against established benchmarks through continuous monitoring activities outlined within their System Security Plan (SSP).
By following these steps diligently and maintaining clear lines of communication throughout each phase of the authorization process, organizations can navigate through FedRAMP successfully and gain valuable trust from government customers.
How to Prepare for Authorization?
Preparing for agency authorization under the FedRAMP program is a crucial step in ensuring that your cloud service offering meets the necessary security requirements. This preparation phase involves a thorough assessment of your system's security controls, documentation, and processes to ensure compliance with the FedRAMP.
To begin, your organization must establish a solid understanding of the FedRAMP requirements and guidance documents provided by the FedRAMP Program Management Office (PMO). These resources will serve as your organization’s roadmap throughout the preparation process. It is also important to identify any gaps in your organization’s current security posture by conducting an initial self-assessment.
Once your organization has identified areas for improvement, it's time to develop a comprehensive System Security Plan (SSP) that outlines how your organization will meet all applicable controls and safeguards. This plan must include detailed descriptions of your system architecture, data flows, risk management strategies, incident response procedures, and contingency plans.
In addition to developing an SSP, your organization will need to implement appropriate technical controls such as encryption mechanisms, access control measures, intrusion detection systems, and logging capabilities. Regular vulnerability assessments and penetration testing are also essential components of this phase.
Another critical aspect of preparation is establishing strong policies and procedures that govern how employees handle sensitive information. Training programs must be implemented to ensure everyone understands their roles and responsibilities when maintaining secure operations within the organization.
By thoroughly preparing for authorization through:
- Careful Documentation Review
- Implementation of Technical Controls
- Establishment of Robust Policies
- and Engaging in Independent Assessments
Your organization can increase your chances of obtaining successful authorization while demonstrating commitment towards securing your cloud services for the federal government.
What are the Phases of the Authorization Process?
- Initiation: The first phase of the agency authorization process involves initiating the request for authorization. This includes identifying the system or service that needs to be authorized and gathering all necessary documentation.
- Security Assessment: Once the initiation phase is complete, a security assessment is conducted to evaluate the system's compliance with FedRAMP requirements. This includes conducting vulnerability scans, penetration testing, and reviewing security controls.
- Remediation: If any vulnerabilities or non-compliant areas are identified during the security assessment, they must be addressed in this phase. Remediation activities may include implementing additional security controls, patching vulnerabilities, or updating policies and procedures.
- Documentation Review: In this phase, all relevant documentation is reviewed by an independent assessor to ensure it meets FedRAMP standards. This includes security plans, risk assessments, test results, and other supporting documents.
- System Authorization: Once all remediation efforts have been completed and documented review has been successfully passed, the system can proceed to authorization stage. This step involves obtaining official approval from a designated authorizing official within the federal agency responsible for granting authority to operate (ATO).
- Maintenance & Continuous Monitoring: After receiving ATO, continuous monitoring activities will commence. As part of ongoing compliance maintenance, periodic assessments such as annual audits, surveillance reviews etc. must be completed to ensure the system complies with FedRAMP requirements.
- Reauthorization: Every three (3) years, the system must undergo a reauthorization process which includes conducting a new security assessment, updating documentation, and obtaining a renewed ATO.
- Termination: If the system is no longer needed or fails to maintain compliance with FedRAMP requirements, the authorization can be terminated by the authorizing agency. This involves revoking the ATO and decommissioning the system.
Each phase plays a vital role in ensuring that systems meet FedRAMP requirements and are authorized for use by federal agencies.
These phases require coordination between various stakeholders including cloud service providers (CSPs), third-party assessors (3PAOs), Joint Authorization Board (JAB), Program Management Office (PMO), and federal agencies.
What are FedRAMP Compliance Requirements?
To achieve FedRAMP compliance, cloud service providers (CSPs) must meet a set of rigorous requirements. These requirements are designed to ensure the security and privacy of federal data in the cloud.
CSPs must adhere to the NIST 800-53 Revision 5 controls, which provide a comprehensive framework for information security. This includes implementing measures such as access control, incident response, and encryption.
In addition to NIST controls, CSPs must also define their system boundary accurately. This involves identifying all components that make up their cloud offering and clearly defining where the provider's responsibilities end and where the customer's begin.
Another crucial requirement is undergoing an independent assessment by a FedRAMP-accredited third-party assessment organization (3PAO). The 3PAO evaluates the CSP's implementation of security controls and assesses its overall compliance with FedRAMP standards.
Furthermore, CSPs must document their policies and procedures in detail. This documentation should outline how they handle risk management, incident response, contingency planning, and other critical aspects of information security.
Continuous monitoring is essential for maintaining FedRAMP compliance. CSPs are required to regularly monitor their systems for vulnerabilities or changes that could impact their security posture. They must also report any incidents or breaches promptly to the appropriate authorities.
By meeting these requirements diligently, CSPs can demonstrate their commitment to safeguarding federal data in accordance with industry best practices. Achieving FedRAMP compliance not only opens doors to government contracts but also instills confidence in customers seeking secure cloud solutions.
How Quzara Can Help?
As a leading provider of cloud-based solutions, Quzara is committed to helping our customers meet the strictest security standards. We are proud to offer our FedRAMP Authorization service, which helps streamline the process of achieving compliance with this important regulation. If you are interested in learning more about our FedRAMP Authorization service, or any of our other security solutions, please contact us today. Our team would be happy to discuss your specific needs and how we can help you protect your data and meet your compliance requirements.



