If your organization is involved in the world of Government Information Technology (IT), chances are you've come across the term "FedRAMP" before. But what exactly is FedRAMP, and why is it so important?
In this blog post, we'll take a deep dive into all things FedRAMP – from understanding its importance to exploring the process of pursuing an agency authorization. So, whether you're a Cloud Service Provider (CSP) looking to obtain agency authorization or an agency seeking guidance on achieving compliance with FedRAMP requirements, this blog will serve as your comprehensive guide through the complexities of FedRAMP. Let's get started!
- What is FedRAMP?
- Why is FedRAMP so Important?
- What is the FedRAMP Authorization Process?
- How can the FedRAMP Authorization Playbook support CSPs?
- What are Post-Authorization Steps?
- What is Continuous Monitoring with FedRAMP Authorizations?
- What are FedRAMP Compliance Requirements?
- What are FedRAMP Compliance Varieties?
- What are the Differences Between FedRAMP and RMF?
- What are the Relationships between FedRAMP and other Federal Compliance Programs?
- Additional Compliance Programs related to FedRAMP
- How Quzara Can Help?
What is FedRAMP?
FedRAMP is a government-wide initiative that sets the standard for cloud security for federal agencies and CSPs that support them. It was established to streamline and improve the authorization process for CSPs seeking to work with government entities. FedRAMP also helps build trust among potential customers by showcasing your organization’s commitment to robust security measures.
The program provides a consistent framework for assessing and authorizing CSP offerings based on NIST 800-53 Revision 5 controls. It enables CSPs to undergo an assessment by an accredited third-party assessment organization (3PAO) to demonstrate compliance with these controls.
Why is FedRAMP so Important?
In today's digital age, data security is of utmost importance for both government agencies and commercial organizations. This is where FedRAMP comes into play. FedRAMP provides a standardized approach to architecture, engineering, security assessment, authorization, and continuous monitoring for CSPs.
One of the key reasons why FedRAMP is so important is because it ensures that CSPs meet stringent security requirements set forth by the federal government. By adhering to these standards, CSPs can gain the trust of government agencies and demonstrate their commitment to protecting sensitive information.
Furthermore, FedRAMP helps streamline the procurement process for federal agencies by providing a marketplace where they can easily find authorized cloud services and leverage Authority-To-Operate (ATO) packages issued by other agencies or the Joint Authorization Board (JAB). This not only saves time, but also ensures that agencies are selecting CSPs that have been thoroughly vetted and approved. In return, obtaining FedRAMP authorization opens the door to opportunities for CSPs to work with various federal agencies. Many government organizations require vendors to have a FedRAMP Authorization to ensure compliance with data protection regulations.
Furthermore, through its continuous monitoring program, FedRAMP ensures ongoing compliance with security controls even after an initial authorization has been granted. This proactive approach helps identify any potential vulnerabilities or risks and allows for timely remediation actions.
The importance of FedRAMP cannot be overstated in today's evolving cybersecurity landscape. It provides a framework for ensuring the confidentiality, integrity, and availability of sensitive data and best practices, while enabling collaboration between government agencies and trusted cloud service providers.
What is the FedRAMP Authorization Process?
The Authorization Process is a crucial step in obtaining FedRAMP Agency Authorization. Once a Cloud Service Provider (CSP) has completed their documentation and prepared their system for assessment, they can move forward with the authorization process.
During this phase, the CSP will submit their System Security Plan (SSP) to the agency sponsor or Joint Authorization Board (JAB) (if selected). The SSP outlines how the CSP implements security controls based on NIST 800-53 Revision 5 guidelines. Additional guidelines on top of the NIST 800-53 Revision 5 maybe be required to be followed on an agency-by-agency basis.
Once submitted, the agency sponsor or JAB will review the SSP and conduct an initial assessment of the system. This may include interviews and document reviews to ensure compliance with FedRAMP requirements.
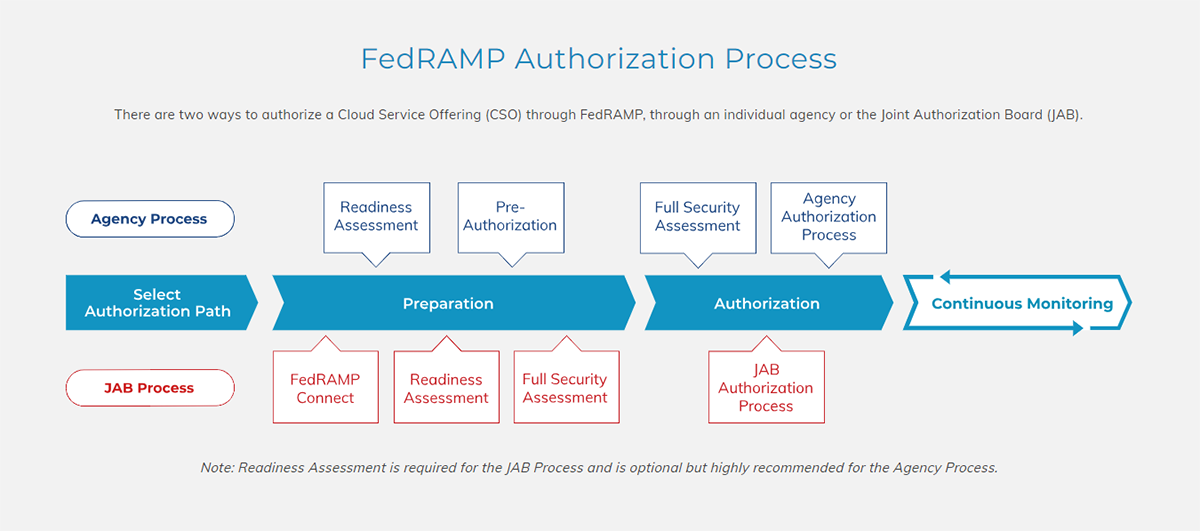
If any issues are identified during this assessment, the CSP will need to address them before moving forward. Once all issues are resolved, the agency sponsor or JAB will grant an Authority to Operate (ATO).
Throughout this process, open communication between all parties involved is key. It's essential for both CSPs and agencies to collaborate effectively to achieve successful authorization within a reasonable timeframe.
However, it's important to note that achieving FedRAMP compliance is not a one-time event but rather an ongoing commitment. Once authorized, CSPs must continually monitor their system’s performance against established benchmarks through continuous monitoring activities outlined within their System Security Plan (SSP).
By following these steps diligently and maintaining clear lines of communication throughout each phase of the authorization process, organizations can navigate through FedRAMP successfully and gain valuable trust from government customers.
How can the FedRAMP Authorization Playbook support CSPs?
FedRAMP Agency Authorization Playbook is a comprehensive resource that provides guidance to federal agencies on how to navigate the complex process of obtaining a FedRAMP authorization. This playbook serves as a roadmap, outlining the steps and requirements for achieving compliance with FedRAMP standards.
The playbook covers various topics such as the roles and responsibilities of different stakeholders involved in the authorization process, including Federal Risk and Authorization Management Program (FedRAMP) PMO and JAB, Cloud Service Providers (CSPs), and federal agencies. It also highlights the relationships between FedRAMP and other federal compliance programs, emphasizing the importance of integration and alignment.
Furthermore, the playbook delves into specific requirements for FedRAMP compliance, detailing key areas such as security controls based on NIST 800-53 Revision 5 guidelines. It provides insights into boundary definition, which plays a crucial role in determining what components are within or outside the scope of an agency's system.
Additionally, it outlines different types of FedRAMP compliance levels available to CSPs based on their security implementations; at the Low, Moderate, or High Impact Level. These distinctions help agencies choose cloud services that align with their security needs.
Moreover, one essential aspect covered by this playbook is continuous monitoring. Once an agency achieves authorization status, it must continuously monitor its systems to ensure ongoing compliance with FedRAMP requirements. The playbook emphasizes this critical step in maintaining security posture over time.
In conclusion, FedRAMP Agency Authorization Playbook acts as a valuable resource for federal agencies navigating through the complex world of cloud computing and ensuring secure data management practices. By following its guidance and leveraging its insights, agencies can streamline their path toward achieving FedRAMP.
What are Post-Authorization Steps?
Once a cloud service provider (CSP) receives their FedRAMP agency authorization, the work doesn't stop there. In fact, it's just the beginning of a new phase in their journey towards maintaining compliance and ensuring the security of their systems.
One crucial step after obtaining agency authorization is continuous monitoring. This involves conducting regular assessments to ensure that all security controls are functioning effectively, and any vulnerabilities or incidents are promptly addressed. CSPs must also provide ongoing reports to the FedRAMP Program Management Office (PMO) or Joint Authorization Board (JAB), demonstrating their adherence to the required standards.
CSPs need to stay up-to-date on any changes or updates made by FedRAMP. It is essential for CSPs to monitor the program's guidance and requirements closely so they can adapt as needed and maintain compliance.
Post-authorization steps are critical in maintaining FedRAMP compliance and continuously improving security practices. By staying vigilant through continuous monitoring, keeping up to date on program guidance, engaging 3PAOs for independent audits, and fostering open communication with customers; CSPs can demonstrate their commitment towards providing secure cloud services within federal agencies' environments.
What is Continuous Monitoring with FedRAMP Authorizations?
Once a CSP receives their FedRAMP authorization, the work doesn't stop there. In fact, it's just the beginning. Continuous monitoring is an essential aspect of maintaining compliance and ensuring the security of federal information in the cloud.
FedRAMP requires CSPs to implement ongoing monitoring practices that align with NIST guidelines. This includes regularly assessing security controls to identify any vulnerabilities or changes that may impact the system's security posture.
One key component of continuous monitoring is conducting vulnerability scanning and assessments on a regular basis. This helps detect and address potential weaknesses in the system promptly. CSPs must also perform penetration testing to evaluate their infrastructure for any exploitable vulnerabilities.
In addition, CSPs are required to provide incident response capabilities as part of their continuous monitoring efforts. This involves having procedures in place to respond effectively in case of a security incident or breach.
Furthermore, CSPs need to continuously monitor their systems for unauthorized access attempts or suspicious activities through log analysis and intrusion detection mechanisms.
Continuous monitoring ensures that agencies can have confidence in the ongoing security of cloud services they utilize. It allows for timely identification and remediation of any issues that may arise over time.
By adhering to these continuous monitoring requirements, CSPs demonstrate their commitment to maintaining a secure environment for federal data within the cloud ecosystem.
What are FedRAMP Compliance Requirements?
To achieve FedRAMP compliance, cloud service providers (CSPs) must meet a set of rigorous requirements. These requirements are designed to ensure the security and privacy of federal data in the cloud.
CSPs must adhere to the NIST 800-53 Revision 5 controls, which provide a comprehensive framework for information security. This includes implementing measures such as access control, incident response, and encryption.
In addition to NIST controls, CSPs must also define their system boundary accurately. This involves identifying all components that make up their cloud offering and clearly defining where the provider's responsibilities end and where the customer's begin.
Another crucial requirement is undergoing an independent assessment by a FedRAMP-accredited third-party assessment organization (3PAO). The 3PAO evaluates the CSP's implementation of security controls and assesses its overall compliance with FedRAMP standards.
Furthermore, CSPs must document their policies and procedures in detail. This documentation should outline how they handle risk management, incident response, contingency planning, and other critical aspects of information security.
Continuous monitoring is essential for maintaining FedRAMP compliance. CSPs are required to regularly monitor their systems for vulnerabilities or changes that could impact their security posture. They must also report any incidents or breaches promptly to the appropriate authorities.
By meeting these requirements diligently, CSPs can demonstrate their commitment to safeguarding federal data in accordance with industry best practices. Achieving FedRAMP compliance not only opens doors to government contracts but also instills confidence in customers seeking secure cloud solutions.
What are FedRAMP Compliance Varieties?
When it comes to achieving FedRAMP compliance, there are different paths that cloud service providers (CSPs) can take. The two main types of FedRAMP compliance are known as "In-Process" and "FedRAMP Authorized".
The In-Process designation is given to CSPs who have initiated the authorization process but have not yet received full agency authorization. This status allows CSPs to market their services as being in the process of becoming FedRAMP compliant.
On the other hand, a CSP that has successfully completed the entire authorization process receives the coveted "FedRAMP Authorized" status. This means that they have met all the rigorous security requirements outlined by FedRAMP and have been granted an Authority To Operate (ATO).
It's important to note that even with In-Process or Authorized status, CSPs must still maintain ongoing compliance through continuous monitoring and regular assessments.
Additionally, within these types of compliance designations, there are also different levels based on impact categories: Low Impact, Moderate Impact, and High Impact. These levels indicate the potential risk associated with a specific system or service.
Achieving any level of FedRAMP compliance requires thorough documentation, implementation of security controls outlined in NIST 800-53 Revision 5 guidelines, and adherence to strict boundary definitions for systems.
Understanding these different types of FedRAMP compliance can help CSPs navigate their journey towards securing agency authorizations and providing trusted cloud services to federal agencies. By following established processes and meeting stringent requirements, organizations can demonstrate their commitment to data security and gain credibility in government markets.
What are the Differences Between FedRAMP and RMF?
When it comes to federal compliance programs, two acronyms that often get thrown around are FedRAMP and RMF. While they both serve the purpose of ensuring the security of government information systems, there are some key differences between the two.
Let's start with what each acronym stands for. FedRAMP stands for Federal Risk and Authorization Management Program, while RMF stands for Risk Management Framework.
FedRAMP is specifically designed for cloud service providers (CSPs) who wish to offer their services to federal agencies. It provides a standardized approach to security assessment, authorization, and continuous monitoring of cloud products and services. On the other hand, RMF is a broader framework that applies to all federal information systems.
Another difference lies in their scope and focus. While RMF covers all aspects of risk management within an organization's IT infrastructure, including policies, procedures, and controls; FedRAMP focuses primarily on assessing the security of cloud-based solutions.
Additionally, there is a difference in terms of implementation timelines. The RMF process can be lengthy as it involves multiple steps such as categorization, selection of security controls from NIST Special Publication 800-53 Revision 5 (the foundation for both frameworks), implementation verification testing (IVT), etc. In contrast, FedRAMP streamlines this process by providing pre-approved baseline security controls that CSPs must align with.
Furthermore, one notable distinction is sponsorship involvement. In the case of RMF authorizations to operate (ATO), individual agencies sponsor or authorize their own systems based on their unique mission requirements. However, in FedRAMP authorizations known as Joint Authorization Board (JAB) authorizations; a group consisting of CIOs from DHS, CDO at GSA, and DOD surveillance sponsors system-level ATOs before granting entry into the marketplace.
In conclusion, FedRAMP and RMF may share similarities in terms of their focus on risk management.
What are the Relationships between FedRAMP and other Federal Compliance Programs?
As a comprehensive security assessment and authorization program, FedRAMP works alongside other federal compliance programs to ensure the highest level of cybersecurity for government agencies. While each program has its own specific requirements, they often overlap in terms of goals and objectives.
One important relationship is with the National Institute of Standards and Technology (NIST) 800-53 Revision 5. This document provides a catalog of security controls that are used as a foundation for many federal compliance programs, including FedRAMP. By aligning with NIST standards, FedRAMP ensures consistency across different government initiatives.
Another key relationship is with the Risk Management Framework (RMF). RMF is a structured process developed by NIST to help organizations manage risk effectively. Although similar in nature, there are differences between RMF and FedRAMP. While RMF focuses on individual systems within an organization, FedRAMP looks at cloud service providers.
It's also worth noting that some federal compliance programs may require additional assessments or certifications beyond what is covered by FedRAMP. However, achieving FedRAMP compliance can be advantageous when pursuing these other programs (including DoD Impact Levels) since it demonstrates adherence to stringent security standards.
By understanding these relationships between FedRAMP and other federal compliance programs and frameworks, organizations can navigate the complex landscape more effectively while ensuring their systems meet all necessary requirements for securing sensitive government data.
Additional Compliance Programs related to FedRAMP:
In addition to the Federal Risk and Authorization Management Program (FedRAMP), there are other compliance programs that organizations might need to consider when it comes to meeting federal cybersecurity requirements. These programs can help ensure that an organization's systems and data are adequately protected.
- National Institute of Standards and Technology (NIST) Special Publication 800-171: Which focuses on protecting Controlled Unclassified Information (CUI). This publication provides guidelines for safeguarding sensitive information and outlines specific security controls that must be implemented.
- Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204-7012: This clause requires contractors who handle Covered Defense Information (CDI) to implement certain cybersecurity measures outlined in NIST SP 800-171.
- International Traffic in Arms Regulations (ITAR): A United States regulatory regime to restrict and control the export of defense and military related technologies to safeguard U.S. national security and further U.S. foreign policy objectives.
It's worth noting that while the aforementioned compliance programs have their own unique requirements, they often overlap with FedRAMP in terms of security controls. Therefore, leveraging existing certifications or authorizations obtained through these programs can help streamline the process of obtaining a FedRAMP authorization.
By understanding and addressing these additional compliance programs, organizations can demonstrate their commitment to maintaining strong cybersecurity practices, bolstering trust among government agencies and potential customers alike.
How Quzara Can Help?
As a leading provider of cloud-based solutions, Quzara is committed to helping our customers meet the strictest security standards. We are proud to offer our FedRAMP Authorization service, which helps streamline the process of achieving compliance with this important regulation. If you are interested in learning more about our FedRAMP Authorization service, or any of our other security solutions, please contact us today. Our team would be happy to discuss your specific needs and how we can help you protect your data and meet your compliance requirements.



