Introduction
Are you harnessing the full power of Microsoft Sentinel while keeping your costs in check? As organizations increasingly rely on Security Information and Event Management (SIEM) solutions like Microsoft Sentinel to protect their digital assets, understanding cost optimization strategies becomes crucial.
In this blog post, we'll dive into the world of Microsoft Sentinel pricing and billing, helping you gain clarity on how you're charged for using this powerful tool. We'll also explore effective ways to plan costs and estimate your billing accurately before diving into its usage. Additionally, we'll share insider tips for maximizing cost efficiency through clever tactics such as utilizing free data sources and optimizing data retention.
But it's not just about saving money; it's about evaluating whether Microsoft Sentinel is truly worth the investment. We'll discuss potential hidden costs that may arise even after resource deletion and examine other services that might impact your bill. Furthermore, we'll address challenges users may encounter along the way, such as understanding complex taxonomy and query language limitations or limited third-party integrations.
Armed with all these insights, we will help you evaluate whether Microsoft Sentinel aligns with your organization's requirements compared to alternative solutions like Logpoint. So let's dive in together and master the art of cost optimization with Microsoft Sentinel!
Understanding Microsoft Sentinel Pricing and Billing
Microsoft Sentinel offers a range of pricing options to meet the needs of organizations of all sizes. By familiarizing yourself with these pricing structures, you can make informed decisions about your investment in the platform.
When it comes to how you're charged for Microsoft Sentinel, there are a few key factors to consider. First, you'll be billed based on the amount of data ingested into the system. This includes both logs from Azure services and external sources such as security appliances.
To simplify pricing, Microsoft has introduced tiered plans that offer different levels of functionality at varying price points. The tiers include Free, Pay-as-you-go, and Capacity Reservation options. Each tier provides increasing capabilities and benefits depending on your organization's specific requirements.
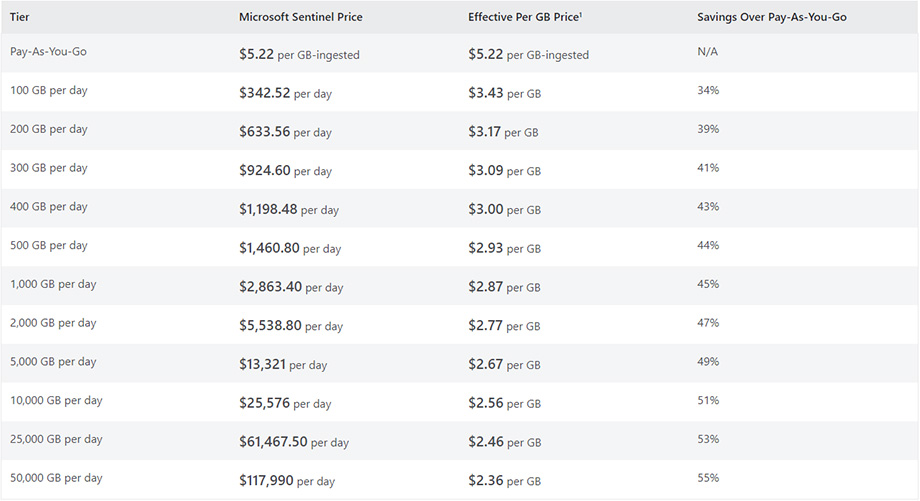
To better understand your Microsoft Sentinel bill, it's important to review its components carefully. Take note of data ingestion costs, which are determined by the volume and type of data being processed. Additionally, consider any additional charges related to long-term log retention or archived logs storage.
By identifying your primary data sources and estimating costs accordingly before using Microsoft Sentinel, you can effectively plan for potential expenses associated with utilizing the platform's features.
In order to maximize cost efficiency when using Microsoft Sentinel, take advantage of free data sources whenever possible. These may include built-in Azure services like Microsoft Entra ID sign-ins or Office 365 audit logs that don't incur additional charges but still provide valuable insights into your security posture.
Another way to optimize costs is by carefully managing your data retention settings and archiving older logs that are no longer needed for real-time analysis. By adjusting log retention policies based on compliance requirements and business needs, you can minimize unnecessary storage costs without sacrificing critical information.
Additionally, be mindful of other Common Event Format (CEF) ingestion costs beyond standard log ingestion rates. For example, some CEF-based sources such as Cisco Firepower sensors may require additional fees which can significantly impact overall cost.
By familiarizing yourself with Microsoft Sentinel pricing and billing components, you can make informed decisions about how to best leverage the platform for your organization's security needs.
Planning Costs and Estimating Billing
When it comes to optimizing your investment in Microsoft Sentinel, planning costs and estimating billing is crucial. By understanding the data sources you'll be utilizing and estimating the associated costs, you can ensure that you're maximizing your budget effectively.
It's important to identify the data sources that will be integrated into Microsoft Sentinel. This could include logs from various applications, servers, or security appliances. By knowing which data sources you'll be using, you can plan costs accordingly and avoid any surprises when the bill arrives.
Estimating costs and billing before diving into Microsoft Sentinel is also essential. Take advantage of tools like Azure Pricing Calculator or consult with a Microsoft representative to get an accurate estimate of what your usage might cost. This way, you can make informed decisions about resource allocation and set realistic budgets for your organization.
Remember that cost optimization doesn't mean compromising on security or functionality. It's about finding a balance between meeting your organization's needs while minimizing unnecessary expenses. By carefully planning costs and estimating billing for Microsoft Sentinel, you can ensure that every dollar spent is utilized effectively towards protecting your assets from potential threats.
Identify Data Sources and Plan Costs Accordingly
Identifying the right data sources is crucial for effectively managing costs in Microsoft Sentinel. Before diving into the platform, take the time to evaluate your organization's needs and prioritize which data sources are most important for your security operations.
Start by examining your existing infrastructure and determine what logs or telemetry you currently have available. This could include firewall logs, network traffic data, endpoint logs, or cloud service activity logs. Understanding what types of data you already have will help you estimate the potential volume and cost of ingesting that information into Microsoft Sentinel.
Next, consider any additional data sources that may be valuable for detecting threats and monitoring security events. These could include cloud provider logs, application logs, DNS traffic records, or even threat intelligence feeds. Assessing these additional sources will give you a clearer picture of how much data needs to be processed and logged within Microsoft Sentinel.
Once you've identified your targeted data sources, it's essential to plan costs accordingly. Take advantage of tools provided by Microsoft Sentinel to estimate ingestion costs based on anticipated log volumes and retention periods. This can help you project monthly expenditures more accurately.
Consider implementing filtering mechanisms such as custom log queries or event filters within Azure Log Analytics before sending all collected raw log files to Microsoft Sentinel. By reducing unnecessary noise upfront through pre-filtering techniques, you can minimize storage costs while still capturing relevant security events.
Remember that optimizing cost efficiency is an ongoing process. Regularly review your chosen data sources and reassess their value over time as business needs evolve. By continuously evaluating and refining your approach to identifying critical information assets in conjunction with thoughtful planning around cost estimation strategies, organizations can effectively optimize their investments in Microsoft Sentinel without compromising security outcomes
Maximizing Cost Efficiency
When it comes to cost optimization, Microsoft Sentinel offers several strategies to help you get the most out of your investment. One way to maximize cost efficiency is by utilizing free data sources. By leveraging built-in connectors and integrating with Azure services like Security Center and Office 365, you can tap into valuable security data without incurring any additional costs.
Another area to focus on for cost optimization is optimizing data retention and archived logs costs. With Microsoft Sentinel, you have control over how long you retain your log data, allowing you to balance storage costs with compliance requirements. By regularly reviewing and adjusting your retention policies based on business needs, you can minimize unnecessary expenses.
Additionally, minimizing other CEF ingestion costs can contribute significantly to overall cost efficiency. CEF ingestion refers to the process of importing third-party logs into Microsoft Sentinel for analysis. To reduce these costs, consider prioritizing essential logs from critical systems rather than ingesting every available log source.
By implementing these strategies for maximizing cost efficiency in Microsoft Sentinel, organizations can effectively manage their budget while still benefiting from advanced threat detection capabilities and streamlined incident response processes. The key is understanding the various options available within the platform and aligning them with specific business requirements.
Remember that mastering cost optimization is an ongoing process that requires regular evaluation and adjustment as your organization's needs evolve over time. Stay vigilant in monitoring usage patterns and making informed decisions about which features are worth investing in based on their impact on security operations.
Utilizing Free Data Sources
Utilizing free data sources is a smart strategy for maximizing cost efficiency when using Microsoft Sentinel. By leveraging the wealth of free data available, organizations can minimize their expenses while still gaining valuable insights from their security monitoring efforts.
One such free data source is Microsoft Entra ID (Formerly Azure Active Directory) logs. AAD provides detailed information about user activity and sign-ins, enabling you to detect suspicious login attempts or unauthorized access. These logs are readily available within your Azure portal and can be easily integrated into Microsoft Sentinel for analysis.
Another valuable source of free data is Office 365 audit logs. These logs capture a wide range of activities performed by users in various Office 365 services, including Exchange Online, SharePoint Online, and Teams. By analyzing these logs in Microsoft Sentinel, you can gain visibility into user behavior and identify potential security incidents.
Additionally, many cloud providers offer native integration with Microsoft Sentinel at no extra cost. For example, AWS CloudTrail provides detailed event records for actions taken within your AWS environment, which can be ingested into Microsoft Sentinel without any additional charges.
By taking advantage of these free data sources, organizations can significantly reduce their overall costs while still benefiting from robust security monitoring capabilities. It's important to explore all available options before investing in external paid solutions to ensure maximum cost optimization with Microsoft Sentinel.
Optimizing Data Retention and Archived Logs Costs
One key aspect of cost optimization in Microsoft Sentinel is optimizing data retention and archived logs costs. Storing large amounts of data can quickly drive up your expenses, so it's essential to strike a balance between the need for historical data and managing costs effectively.
To start, carefully evaluate your organization's requirements for retaining log data. Determine which types of logs are necessary to keep for compliance or investigation purposes, and consider setting up different retention policies based on their importance. By prioritizing critical logs and implementing shorter retention periods for less significant ones, you can reduce storage costs without sacrificing essential information.
Another strategy involves leveraging Azure Blob Storage tiering options. By utilizing hot storage for frequently accessed logs and transitioning older or less frequently used logs to cool or archive tiers, you can take advantage of lower-cost storage options while still maintaining accessibility when needed.
Additionally, consider implementing intelligent filtering mechanisms within Microsoft Sentinel. This allows you to avoid ingesting unnecessary data into the system, further reducing costs associated with storing irrelevant or redundant information.
Regularly monitoring and reviewing your log ingestion rates is crucial as well. Analyzing patterns in the volume of incoming logs can help identify any unexpected spikes that may indicate misconfigured logging sources or potential security incidents. Addressing these issues promptly not only helps optimize costs but also improves overall system performance.
By employing these strategies to optimize data retention and archived logs costs within Microsoft Sentinel, organizations can maximize the value they derive from the platform while keeping expenses under control
Minimizing Other CEF Ingestion Costs
When it comes to cost optimization in Microsoft Sentinel, it's important to look beyond the obvious expenses and identify areas where you can minimize your spending. One area that often goes overlooked is the costs associated with ingesting CEF data.
To minimize these ingestion costs, one strategy is to carefully evaluate the necessity of ingesting all CEF logs into Sentinel. By filtering out unnecessary or redundant logs, you can reduce both storage and processing costs. This involves understanding your organization's specific logging requirements and defining clear criteria for what should be ingested.
Additionally, consider optimizing your log collection process by leveraging built-in connectors or custom parsers that allow you to ingest only relevant fields from CEF logs. This selective ingestion approach decreases the amount of data being processed and stored, ultimately reducing overall costs.
Another way to minimize CEF ingestion costs is by utilizing compression techniques for log files. Compressing log files before ingestion reduces their size, resulting in lower storage requirements as well as reduced network bandwidth consumption during data transfer.
Furthermore, regular monitoring and fine-tuning of your log ingestion configurations can help identify any inefficiencies or unnecessary duplication in event collection processes. By continuously optimizing these configurations based on actual usage patterns and business needs, you can further lower your overall CEF ingestion costs.
Minimizing other CEF ingestion costs within Microsoft Sentinel requires careful consideration of which logs are necessary for analysis and taking steps such as filtering out redundant logs, employing selective parsing techniques, compressing log files before ingestion, and regularly reviewing configuration settings for optimization opportunities. By implementing these strategies effectively, organizations can maximize their investment in Microsoft Sentinel while keeping their cost footprint under control.
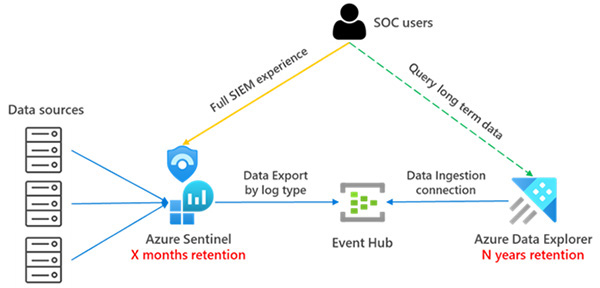
Azure Data Explorer
Also, consider using Azure Data Explorer (ADX) for log data storage instead of traditional storage solutions.
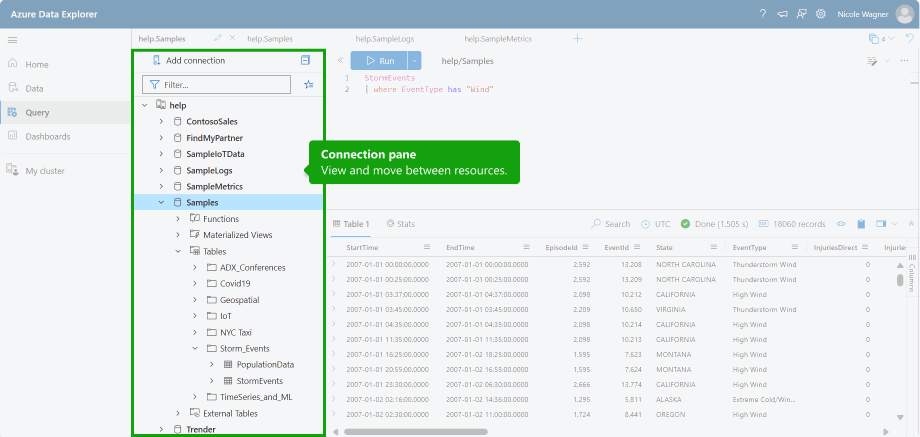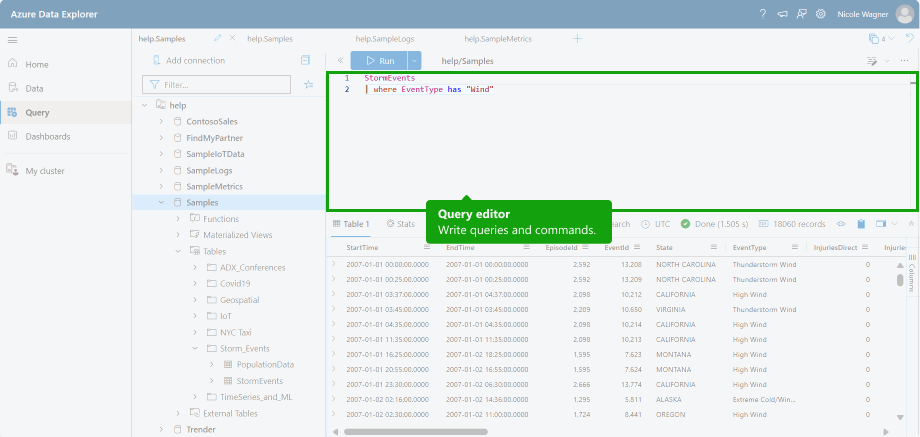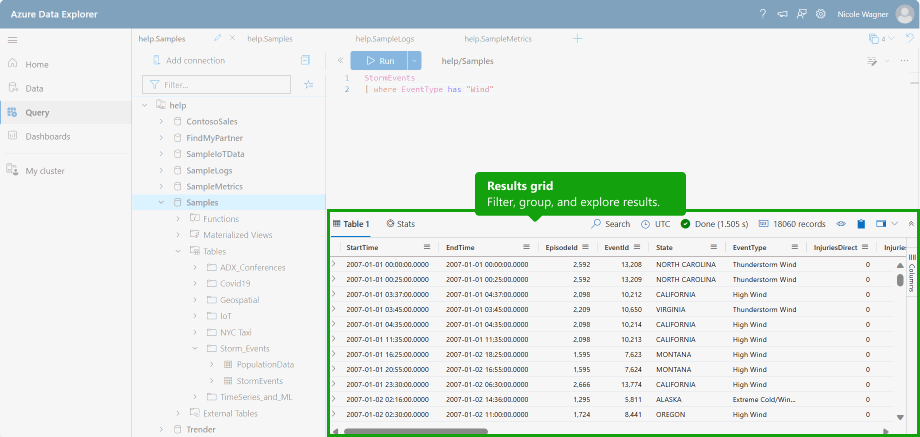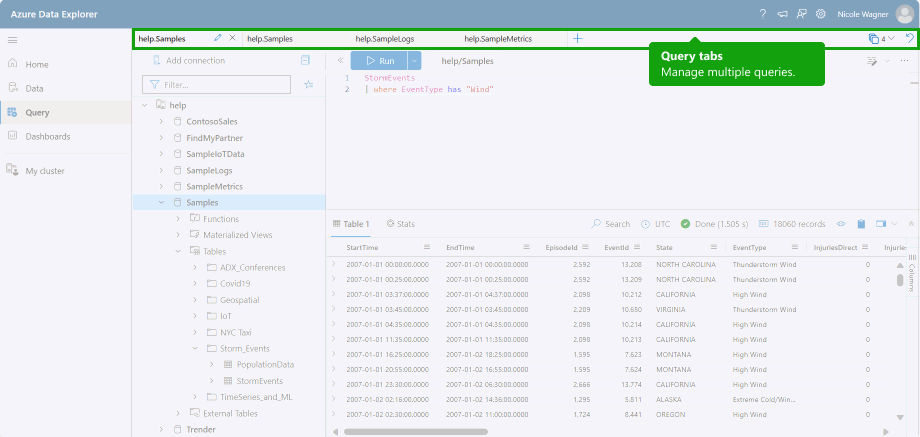
ADX is optimized for high-performance analytics and can significantly reduce storage costs. Lower value security can be routed to ADX, while high-value data can be stored in a Sentinel. Data within ADX can be queried using the Kusto query language(KQL) from Sentinel or the ADX Interface.
Security teams can use Machine Learning and AI analytics on ADX clusters with capabilities such as KQL functions, Jupyter Notebooks, and Azure Synapse.
Finally, data in Sentinel can be offloaded into ADX after the 90-day free storage period, ensuring all logs can be queried for their entire life cycle.
Another benefit of storing your organization's security logs within ADX is the ability to provide rapid access to third parties for Incident Response, Threat Hunting, or Data Science analytics.
Read-only access is easily granted to third parties using temporary Role Based Access Control (RBAC) policies.
Transferring data between SIEMs, Data Lakes, and Application Servers for the purpose of reactive investigations or ad-hoc threat hunting is a process of the past and can quickly become costly.
ADX in combination with RBAC provides the flexibility to let external security teams analyze data where it resides - within ADX.
Potential Hidden Costs
When it comes to managing the cost of Microsoft Sentinel, there are a few potential hidden expenses that you need to be aware of. One such cost is the possibility of incurring charges even after deleting resources. This can occur if logs or other data sources are not properly configured for deletion, leading to ongoing storage costs.
Additionally, it's important to keep in mind that while Microsoft Sentinel itself has its own pricing structure, there may be additional costs associated with other services that you choose to integrate with. For example, if you decide to use third-party tools or applications alongside Microsoft Sentinel, there may be separate fees or licensing requirements.
To ensure cost optimization and avoid unexpected expenses, it's crucial to closely monitor your usage and regularly review your billing statements. By staying vigilant and proactive in managing your Microsoft Sentinel deployment, you can minimize any potential hidden costs and maximize the value of your investment.
Remember that understanding the full scope of costs associated with using Microsoft Sentinel will help you make informed decisions about its worth and benefits for your organization. So stay informed and take advantage of all available resources when evaluating the true cost-effectiveness of this powerful security solution.
Costs that Might Accrue After Resource Deletion
When it comes to managing costs in Microsoft Sentinel, it's essential to consider the potential expenses that may arise even after deleting resources. While you may think removing a resource would eliminate all associated costs, there are a few factors to keep in mind.
Data retention and storage costs can continue even after resource deletion. If you had enabled long-term data retention or archived logs before removing a resource, you may still incur charges for storing that data. It's crucial to review your retention policies and ensure they align with your cost optimization goals.
Another consideration is any lingering ingested events or queries running against deleted resources. Even if you delete an Azure Monitor Log Analytics workspace used by Microsoft Sentinel, the events ingested during its usage will remain stored within Azure Monitor until their respective retention periods expire.
Be aware of any indirect costs related to other services integrated with Microsoft Sentinel. For example, integrating third-party solutions like Threat Intelligence Platforms or SIEM systems could come with additional licensing fees or usage charges outside of the core Microsoft Sentinel pricing structure.
By carefully analyzing these potential post-deletion costs and factoring them into your overall cost optimization strategy for Microsoft Sentinel, you can make informed decisions about resource management and avoid unexpected expenses down the road.
Costs and Pricing for Other Services
Costs and pricing for other services can be an important consideration when evaluating Microsoft Sentinel's overall cost optimization. While the pricing structure for Microsoft Sentinel itself is relatively transparent, it's essential to understand any additional costs that may arise from using complementary services.
One potential area where costs can vary is in data ingestion. Depending on your organization's needs, you may choose to integrate third-party tools or services with Microsoft Sentinel. However, it's crucial to be aware that these integrations might come with their own costs and billing structures.
Another factor to consider is the storage and retention of logs. If you have a large volume of data or require longer retention periods, there may be additional charges associated with storing and archiving logs beyond what is included in your base subscription.
Additionally, if you rely on external threat intelligence feeds or premium connectors for enhanced functionality within Microsoft Sentinel, these features could also incur extra fees.
Evaluating the Worth of Microsoft Sentinel
When considering any investment, it is essential to evaluate its worth. The same goes for Microsoft Sentinel. Is it worth the cost? Let's delve into this question.
Microsoft Sentinel offers a comprehensive set of features that can greatly enhance your organization's security operations. Its advanced threat detection capabilities and real-time monitoring enable proactive threat response and incident management.
Furthermore, by harnessing the power of artificial intelligence and machine learning, Microsoft Sentinel provides valuable insights and helps identify patterns that may go unnoticed otherwise. This allows for faster detection and response to potential threats.
Another aspect to consider is the seamless integration with other Microsoft services such as Microsoft Entra ID and Office 365. This integration streamlines security operations and enables centralized visibility across multiple platforms.
In terms of cost-effectiveness, comparing alternatives like Logpoint or Splunk can provide helpful context. While these solutions may offer similar functionalities, they often come at a higher price point.
However, it's crucial to acknowledge some challenges associated with using Microsoft Sentinel. The complex taxonomy and query language might require additional training or expertise upfront. Additionally, third-party integrations are limited compared to other SIEM tools in the market.
To truly determine if Microsoft Sentinel is worth the investment for your organization, conducting a thorough evaluation tailored to your specific needs is recommended. Consider factors such as scalability requirements, existing infrastructure compatibility, and desired outcomes from implementing a SIEM solution.
Each organization will weigh these factors differently based on their unique circumstances. It’s important to gather all necessary information before making an informed decision about investing in Microsoft Sentinel or exploring alternative solutions available in today’s market.
Overcoming Challenges and Complexities
When it comes to mastering cost optimization with Microsoft Sentinel, there are certain challenges and complexities that you may encounter along the way. Understanding these obstacles can help you navigate them effectively.
One challenge is understanding the complex taxonomy and query language used in Microsoft Sentinel. The platform uses its own unique query language called KQL. While powerful, it can be daunting for users who are not familiar with it. However, investing time in learning KQL will pay off as it allows you to write advanced queries and get more specific results.
Another complexity lies in the limited third-party integrations available with Microsoft Sentinel. While the platform offers integration options with popular services like Microsoft Entra ID and Office 365, some organizations may require additional integrations that are not readily available. It's important to assess your organization's specific needs before committing to Microsoft Sentinel.
Despite these challenges, Microsoft Sentinel remains a robust solution for security monitoring and threat detection. With proper training and support from the Microsoft community, many of these complexities can be overcome. By leveraging its strong capabilities and staying up-to-date on new features, you can maximize your investment in this powerful tool.
Remember that each organization has different requirements when it comes to security monitoring solutions. It's crucial to evaluate how well Microsoft Sentinel aligns with your organization's needs before making a decision. Additionally, comparing alternative solutions like Logpoint or other SIEM platforms can provide valuable insights into which option suits your requirements best.
Understanding the Complex Taxonomy and Query Language
Understanding the complex taxonomy and query language in Microsoft Sentinel is crucial for effectively utilizing this powerful tool. The taxonomy, or categorization of data sources, can be intricate and requires a deep understanding of your organization's infrastructure. By comprehending the different categories and their associated log formats, you can select the appropriate ones to ingest into Sentinel.
Once you have ingested the data, querying it becomes essential for threat detection and investigation. However, mastering the query language may seem daunting at first. It utilizes KQL, which has its own syntax and functions unique to Sentinel.
To overcome these complexities, take advantage of Microsoft's extensive documentation and training resources. There are comprehensive guides available that explain how to navigate through the taxonomy and construct effective queries using KQL.
Additionally, consider joining online communities or forums where users share tips and best practices for working with Sentinel's query language. Engaging with other experienced users can provide valuable insights on how to optimize your queries for maximum efficiency.
By investing time in understanding the complex taxonomy and query language of Microsoft Sentinel, you'll unlock its full potential as a cost-effective security solution for your organization.
Conclusion
In this blog post, we have explored the strategies for mastering cost optimization with Microsoft Sentinel. We started by understanding the pricing and billing structure of Microsoft Sentinel, including how you are charged and the simplified pricing tiers.
We then moved on to planning costs and estimating billing, discussing the importance of identifying data sources and planning costs accordingly. It is crucial to estimate costs and billing before using Microsoft Sentinel to ensure that you stay within your budget.
To maximize cost efficiency, we discussed utilizing free data sources available in Microsoft Sentinel. We also highlighted the significance of optimizing data retention and archived logs costs, as well as minimizing other CEF ingestion costs.
Additionally, we addressed potential hidden costs that might accrue after resource deletion in Microsoft Sentinel. It's essential to be aware of these additional expenses to avoid any surprises down the line.
Next, we evaluated whether Microsoft Sentinel is worth its cost by considering its features, capabilities, and value compared to alternative solutions like Logpoint.
We also acknowledged some challenges and complexities associated with using Microsoft Sentinel. Understanding its complex taxonomy and query language can be a learning curve for users. Additionally, limited third-party integrations may pose some difficulties depending on specific requirements.
For more detailed information on Microsoft Sentinel’s pricing and billing structure as well as tips for cost optimization, check out the following resources:
Next Steps for Cost Optimization
- Continuously Monitor and Analyze Costs: Once you have implemented Microsoft Sentinel, it's crucial to regularly monitor and analyze your costs to identify any areas of potential optimization. Keep a close eye on your billing statements and usage reports to track your spending patterns and ensure that you are getting the most value out of your investment.
- Optimize Data Retention Policies: Review your data retention policies within Microsoft Sentinel and adjust them based on your organization's specific needs. By carefully managing the retention period for different types of logs, you can strike a balance between compliance requirements and cost efficiency.
- Fine-tune Alerting Rules: Refine your alerting rules within Microsoft Sentinel to reduce false positives, which can lead to unnecessary costs associated with investigating non-threatening incidents. Regularly review and update these rules based on feedback from security analysts in order to improve their effectiveness while minimizing unnecessary alerts.
- Leverage Automation: Explore opportunities for automation within Microsoft Sentinel to streamline workflows, increase efficiency, and minimize manual efforts required for managing security operations. Automating repetitive tasks not only saves time but also reduces the overall operational costs associated with incident response.
- Stay Updated on New Features: Keep up-to-date with the latest features and updates released by Microsoft Sentinel as they may offer new functionalities or optimizations that could positively impact cost management strategies. Engage with community forums, attend webinars or training sessions provided by Microsoft so that you can leverage all available tools effectively.
Remember that cost optimization is an ongoing process rather than a one-time task – stay vigilant about monitoring expenses, refining configurations, leveraging automation where applicable, staying informed about new features, and continuously adjusting your approach as needed in order to maximize the value of your investment in Microsoft Sentinel.
Additional resources
To further enhance your understanding of Microsoft Sentinel and its cost optimization strategies, here are some additional resources you can explore:
- Microsoft Documentation: The official documentation provided by Microsoft offers a wealth of information on various aspects of Microsoft Sentinel, including pricing, billing, and cost optimization techniques. It provides detailed guides and tutorials to help you navigate through the platform effectively.
- Community Forums: Engaging with the vibrant community forums dedicated to Microsoft Sentinel can be invaluable in gaining insights from fellow users who have already mastered cost optimization techniques. Here, you can ask questions, share experiences, and learn from real-life scenarios faced by other organizations.
- Webinars and Events: Keep an eye out for webinars and events organized by Microsoft or its partners that specifically focus on optimizing costs with Microsoft Sentinel. These sessions often provide expert advice, best practices, case studies, and interactive discussions that shed light on different approaches to maximizing your investment.
- Blogs and Whitepapers: Stay updated with blogs written by industry experts or whitepapers published by thought leaders in the field of cybersecurity analytics. These resources often delve into specific topics related to cost management in security operations centers (SOCs) using advanced technologies like Microsoft Sentinel.
Remember that continuous learning is key when it comes to mastering any technology solution like Microsoft Sentinel. By exploring these additional resources along with hands-on experience gained through implementation, you can become proficient in effectively optimizing costs while leveraging the full potential of this powerful security tool.
For a more in-depth discussion on how we can assist you, please get in touch with us:



