Introduction
In a world where cyber threats are evolving at lightning speed, it's crucial for organizations to empower their security teams with cutting-edge tools and technologies.
Enter Microsoft Defender for Endpoint and 365 Defender – a powerful duo poised to revolutionize the way we hunt down advanced threats.
Join us as we dive into the captivating world of advanced hunting and explore how these game-changing solutions can unleash your security team's potential like never before. Get ready to embark on an exhilarating journey toward safeguarding your organization against even the most elusive adversaries!
Spotlight: Microsoft 365 Defender & Microsoft Defender for Endpoint
Microsoft 365 Defender and Microsoft Defender for Endpoint are two powerful tools designed to empower security teams in their fight against cyber threats. These solutions are part of the Microsoft Defender suite, a comprehensive set of security tools that work together to protect organizations from various types of attacks.
Introduction to Microsoft 365 Defender:
Microsoft 365 Defender is a unified security platform that brings together the capabilities of three different Microsoft products – Office 365 Advanced Threat Protection (ATP), Azure Advanced Threat Protection (ATP), and Windows Defender ATP. This integration allows for centralized management and visibility across all endpoints, identities, email, and cloud applications.
One of the key benefits of Microsoft 365 Defender is its ability to provide advanced threat protection for an organization's entire digital estate. By collecting data from multiple sources and applying cutting-edge analytics and AI technologies, it can detect sophisticated attacks that may go unnoticed by traditional security measures. This comprehensive approach ensures that every aspect of an organization's digital environment is protected, making it an essential tool for modern-day security teams.
Introduction to Microsoft Defender for Endpoint:
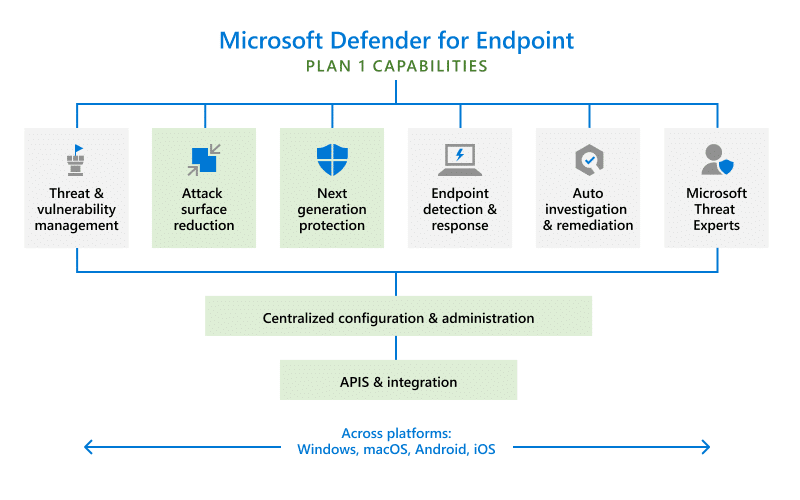
Microsoft Defender for Endpoint is a cloud-based endpoint protection solution that uses next-generation antivirus (NGAV) technology to prevent, detect, investigate, and respond to advanced threats on devices running Windows 10 or later. It provides real-time protection against malicious files, URLs, processes, memory exploits, network connections, and more.
This solution offers several advanced features such as:
- Behavioral analysis: Microsoft Defender for Endpoint continuously monitors device behavior for any suspicious activities and takes immediate action to stop threats.
- Automated investigation and remediation: With the help of AI and machine learning, this solution can automatically investigate alerts, determine the scope and severity of a threat, and take necessary remediation actions without human intervention.
- Endpoint Detection and Response (EDR): Microsoft Defender for Endpoint provides EDR capabilities that allow security teams to quickly investigate and respond to advanced attacks on endpoints.
- Secure Score: This feature helps organizations measure their overall security posture and provides recommendations for improving it.
In summary, Microsoft 365 Defender and Microsoft Defender for Endpoint are two powerful tools that work together to protect an organization's digital environment from a wide range of cyber threats. By leveraging advanced technologies such as AI, machine learning, and behavioral analysis, these solutions provide comprehensive protection against modern-day attacks while also offering proactive detection and automated response capabilities.
Understanding the Need for Advanced Hunting and Investigations in Security Teams
In today's digital landscape, the threat of cyber attacks and security breaches is constantly evolving and becoming more sophisticated. As a result, traditional security measures are no longer enough to protect organizations from these threats. This is where advanced hunting and investigations come into play.
The Evolution of Cyber Threats
The first step in understanding the need for advanced hunting and investigations in security teams is to recognize the evolution of cyber threats. In the past, hackers primarily used basic methods such as malware and phishing attacks to gain access to sensitive data. However, with advancements in technology, cybercriminals have developed more complex techniques that can bypass traditional security measures.
These new methods include fileless attacks, which do not leave any trace on a victim's system, making them difficult to detect. Additionally, attackers now use social engineering tactics to trick employees into divulging confidential information or granting access to their systems.
With such sophisticated tactics being employed by hackers, it has become crucial for organizations to have advanced tools and techniques at their disposal for detecting and responding to these threats effectively.
The Limitations of Traditional Security Measures
Traditional security solutions like firewalls and antivirus software are designed to provide a baseline level of protection against common threats. While these solutions are essential components of a robust security strategy, they often fall short when it comes to detecting advanced threats.
For example, signature-based antivirus programs rely on known patterns or signatures of malicious code to identify threats. This means they can only detect previously identified malware but may miss new or customized attacks.
Similarly, firewalls are effective at blocking known malicious traffic, but they may not be able to identify and block more sophisticated attacks that use legitimate network protocols or encryption techniques to evade detection.
The Role of Advanced Hunting and Investigations
Advanced hunting and investigations refer to the process of proactively searching for threats and investigating potential security incidents within an organization's network and systems. This approach involves using advanced tools, techniques, and expertise to analyze data from various sources and identify anomalies or patterns that could indicate a potential attack.
By continuously monitoring the network for signs of suspicious activity, security teams can detect threats that may have gone undetected by traditional security measures. They can then investigate these incidents further to understand how the attack occurred, what data may have been compromised, and take remediation actions to prevent future attacks.
Benefits of Advanced Hunting and Investigations
- Early Detection of Threats
One of the primary benefits of advanced hunting and investigations is early threat detection. By actively searching for indicators of compromise (IOCs) in real-time, security teams can identify potential threats before they cause significant damage. This allows organizations to respond quickly and prevent attackers from gaining access to sensitive data.
- Proactive Monitoring
This isn't just about defense; it's about understanding the evolving threat matrix and preempting potential vulnerabilities.
Key Features of Microsoft 365 Defender and Microsoft Defender for Endpoint for advanced hunting
The advanced hunting capabilities of Microsoft 365 Defender and Microsoft Defender for Endpoint are powerful tools that provide security teams with comprehensive visibility into their organization's network. These features allow teams to proactively hunt for potential threats, enabling them to stay one step ahead of cybercriminals.
- Custom Queries and Rule Creation
One of the most significant features of advanced hunting is the ability to create custom queries and rules. This feature allows security teams to tailor their searches based on their specific needs and environment. The query language used is easy to learn, making it accessible for any team member regardless of technical expertise.
- Real-Time Visibility
Advanced hunting offers real-time visibility into an organization's network, allowing security teams to monitor events as they happen. By analyzing live data from endpoints, networks, and cloud services, these tools can quickly detect anomalies or suspicious activities and take immediate action.
- Cross-Domain Hunting
Microsoft 365 Defender and Defender for Endpoint allow cross-domain hunting, which means that a single query can be run across multiple domains in an organization simultaneously. This capability ensures a more comprehensive search and provides a holistic view of potential threats across all domains.
- Integration with Threat Intelligence
These advanced hunting tools seamlessly integrate with Microsoft's global threat intelligence feed, providing security teams with access to the latest threat information from around the world. With this integration, organizations can proactively hunt for emerging threats based on known indicators of compromise (IOCs).
- Advanced Filtering Options
To help narrow down search results, advanced hunting offers various filtering options such as time frame, event type, and severity level. This feature helps reduce noise and focus on critical events that require immediate attention.
- Graphical Representation of Data
Advanced hunting tools offer graphical representations of data, making it easier for non-technical team members to understand and interpret the results of a search. These visualizations can also help identify patterns or trends that may be missed with a text-based analysis.
- Scheduled Queries
Security teams can schedule queries to run automatically at specific intervals, allowing for continuous monitoring and detection of potential threats. This feature is especially useful for organizations with limited resources or those looking to automate certain tasks.
- Custom Alert Creation
With advanced hunting, security teams can create custom alerts based on their queries and rules, enabling them to receive real-time notifications when specific conditions are met. This capability allows for quick identification and response to potential threats before they escalate.
- Collaboration Features
Microsoft 365 Defender and Defender for Endpoint offer collaboration features that allow multiple team members to work together on an investigation or hunt. Team members can share queries, rule sets, and investigation notes within the platform, promoting knowledge sharing and efficient teamwork.
- Integration with Other Security Tools
These advanced hunting tools seamlessly integrate with other Microsoft security products, such as Azure Sentinel and Microsoft Cloud App Security. This integration allows for a more comprehensive and coordinated response to potential threats across an organization's entire security ecosystem.
Overall, the advanced hunting capabilities of Microsoft 365 Defender and Defender for Endpoint provide security teams with a powerful set of tools to proactively hunt for potential threats, enabling them to stay ahead of cybercriminals and protect their organization's network.
Setting Up Advanced Hunting with Microsoft 365 Defender: A Step-by-Step Guide
- Enable Microsoft Defender for Endpoint: The first step is to ensure that Microsoft Defender for Endpoint is enabled on your device. This can be done by going to the Microsoft 365 security center, selecting 'Threat management' and then 'Microsoft Defender for Endpoint.'
- Configure data collection: Once Microsoft Defender for Endpoint is enabled, you will need to configure data collection settings to start collecting data from your devices. This can be done by going to the 'Settings' tab in the Microsoft 365 security center and selecting 'Data collection.' Here, you can choose which types of data you want to collect and from which devices.
- Access advanced hunting: To access advanced hunting, go to the 'Hunting' tab in the Microsoft 365 security center and select 'Advanced hunting.' This will take you to the query editor where you can create custom queries based on your specific needs.
- Understand the query language: Advanced hunting uses a specific query language called Kusto Query Language (KQL). It is important to have a basic understanding of this language in order to effectively use advanced hunting. There are many resources available online that provide information on KQL syntax and how it works.
- Utilize pre-defined queries: If you are new to advanced hunting or don't have much experience with KQL, there are pre-defined queries available that cover common scenarios such as detecting malware or suspicious behavior.
- Create custom queries: If you want to create a custom query, click on the 'New query' button and start writing your query in the editor. You can use the autocomplete feature to help you with the syntax and structure of your query.
- Test and refine your query: Once you have written your query, click on the 'Run' button to test it. If there are any errors, they will be displayed, and you can make adjustments to your query until it runs successfully.
- Save and schedule queries: Once you have a working query, you can save it for future use by clicking on the 'Save' button. You can also schedule the query to run at specific times or intervals by clicking on the 'Schedule' button.
- Review results: After running a query, you will see the results displayed in a table format. You can click on individual events to get more details and investigate further if needed.
- Take action: From advanced hunting, you can also take action on selected events such as isolating a device or initiating an investigation in Microsoft Defender for Endpoint.
- Explore other features: Advanced hunting also offers additional features such as visualization tools, pivot tables, and charting options that can help.
Success Story: Real-world Cases of Threat Hunting Using 365 Defender and Microsoft Defender for Endpoint
Threat hunting has become an essential practice for security teams in today’s rapidly evolving threat landscape. It involves proactively searching for and identifying threats that have evaded traditional security measures, with the goal of preventing or mitigating potential attacks. Microsoft Defender for Endpoint (formerly known as Windows Defender ATP) and 365 defender offer powerful tools and capabilities to aid security teams in their threat hunting efforts.
In this section, we will explore some real-world examples of successful threat hunting using 365 defender and Microsoft Defender for Endpoint. These examples showcase how these tools can be leveraged to detect and respond to sophisticated cyber threats.
- Identifying a Stealthy Crypto-Mining Campaign
A large financial institution was experiencing slow system performance across their network, which prompted their security team to conduct a thorough investigation using Microsoft Defender for Endpoint's advanced hunting capabilities. The team discovered a malicious PowerShell script running on several endpoints, which was responsible for mining cryptocurrency without the users' knowledge.
Further analysis revealed that the attackers had used a legitimate tool called CertUtil to download malicious payloads onto the compromised machines, bypassing traditional antivirus solutions. Using 365 defender's behavioral analytics, the team identified additional indicators of compromise (IOCs) related to this attack and took immediate action to remediate the issue before any significant damage could occur.
- Detecting Fileless Malware Through Memory Forensics
A multinational manufacturing company detected unusual network traffic from one of its servers during routine monitoring activities conducted by Microsoft Defender for Endpoint. Upon further investigation , the security team found evidence of a fileless attack in the server's memory, which allowed the attackers to evade traditional antivirus solutions.
To investigate this incident further, the team used advanced hunting in 365 defender to retrieve memory forensics data from the affected server. They were able to identify and block the malicious processes responsible for executing the fileless malware and prevent any data exfiltration.
- Hunting for Ransomware Using Behavioral Analytics
A global logistics company was hit by a widespread ransomware attack that encrypted critical files and demanded a hefty ransom in exchange for decryption keys. The company's security team used Microsoft Defender for Endpoint's behavioral analytics to hunt for indicators of ransomware activity across their network.
The team was able to identify suspicious behaviors such as mass file encryption and attempts to spread laterally within the network. With these insights, they quickly isolated infected machines and stopped the propagation of the ransomware before it could cause significant damage.
- Detecting phishing attacks through email protection
A leading healthcare provider was experiencing a surge in phishing attacks targeting its employees via email. The organization had already deployed Microsoft Defender for Endpoint's email protection capabilities and configured advanced threat protection policies to detect and block malicious emails.
Using 365 defender's reporting and analytics, the security team was able to identify patterns in the phishing emails and track their origins. With this information, they were able to take proactive measures to block future attacks and educate their employees on how to spot and report suspicious emails.
- Investigating a Supply Chain Attack
A government agency discovered that one of its vendors had been breached, potentially exposing sensitive information about their operations. The agency's security team used Microsoft Defender for Endpoint's threat intelligence capabilities to identify any potential signs of compromise within their network.
The team found evidence of a malicious program being executed on several endpoints, which turned out to be part of a broader supply chain attack. They immediately notified the affected vendor and took steps to remediate the issue before any further damage could occur.
These real-world examples demonstrate how 365 defender and Microsoft Defender for Endpoint can be effectively utilized for successful threat hunting. By leveraging these powerful tools, organizations can proactively detect and respond to sophisticated cyber threats and keep their systems safe from evolving attack techniques.
Harnessing Automation for Advanced Investigations
Automation has become an integral part of many industries, and the field of cybersecurity is no exception. With the increasing sophistication of cyber threats, security teams are constantly looking for ways to improve their detection and response capabilities. This is where automation comes into play, offering a range of tools and techniques that can significantly enhance the efficiency and effectiveness of advanced investigations.
Microsoft Defender for Endpoint (formerly known as Microsoft Defender Advanced Threat Protection) and Microsoft 365 Defender Threat Hunting are two powerful tools that leverage automation to strengthen a company's security posture. Let's take a closer look at how these tools can be leveraged to improve advanced investigations.
- Automated Threat Detection
One of the key features of Microsoft Defender for Endpoint is its ability to automatically detect and respond to potential threats in real-time. Leveraging machine learning algorithms and behavioral analytics, this tool continuously monitors endpoints across an organization's network, looking for suspicious activities or behaviors that could indicate a potential threat.
This automated threat detection capability not only helps security teams identify threats faster but also reduces the burden on analysts who would otherwise have to manually sift through large volumes of data. By automating this process, valuable time and resources are saved, allowing security teams to focus on more critical tasks such as investigating and responding to confirmed threats.
- Customizable Playbooks
Microsoft Defender for Endpoint also offers customizable playbooks that allow organizations to define specific actions or responses based on different types of threats. These playbooks can be tailored to an organization's unique environment, policies, and threat landscape, and can be triggered automatically when a threat is detected.
For example, if a malicious file is identified on an endpoint, the playbook can be configured to automatically isolate the affected device from the network, initiate a scan, and remediate the threat. This level of automation not only speeds up response times but also ensures consistency in how threats are handled across an organization.
- Automated Investigation and Remediation
Microsoft 365 Defender Threat Hunting takes automation a step further by offering automated investigation and remediation capabilities. This tool uses machine learning algorithms to analyze data from multiple sources such as endpoints, network logs, and cloud services to identify potential threats.
Once a threat is detected, Microsoft 365 Defender Threat Hunting can automatically initiate an investigation, collect relevant data from various sources, and provide a detailed report with actionable insights for security teams. It can also trigger automated response actions such as quarantining compromised devices or blocking malicious IP addresses.
- Integration with Other Microsoft Tools
Both Microsoft Defender for Endpoint and Microsoft 365 Defender Threat Hunting seamlessly integrate with other Microsoft tools such as Azure Sentinel and Azure Security Center. This allows organizations to leverage the power of automation not just within individual tools but across their entire security ecosystem.
Integrating other security solutions
Integrating other security solutions with Microsoft Defender for Endpoint and Microsoft 365 Defender Threat Hunting can greatly enhance the overall security posture of an organization. These additional solutions, when combined with the advanced capabilities of Microsoft's endpoint protection systems, provide a more comprehensive approach to detecting, analyzing, and responding to cyber threats.
One of the key benefits of integrating other security solutions with Microsoft Defender is the ability to leverage multiple sources of data. By bringing in data from different security tools and platforms, organizations can gain a wider view of their environment and identify potential threats that may have otherwise gone unnoticed. This not only helps in threat detection but also aids in proactive threat hunting and incident response.
There are several ways to integrate other security solutions with Microsoft Defender for Endpoint and Advanced Hunting:
- API Integrations:
One approach is through APIs (Application Programming Interfaces), which allow different software systems to communicate with each other. With Microsoft's open API architecture, organizations can easily integrate third-party security solutions such as SIEMs (Security Information and Event Management), SOARs (Security Orchestration Automation & Response) or TIPs (Threat Intelligence Platforms). These integrations enable the exchange of real-time information between systems, allowing for automated threat detection and response.
- Agent-based Integrations:
collect data from various sources such as network traffic, DNS logs, firewall logs, etc. This data is then fed into Microsoft Defender for Endpoint and Advanced Hunting for analysis and correlation with other endpoint data.
- Threat Intelligence Feeds:
Integrating threat intelligence feeds with Microsoft Defender can also enhance its capabilities by providing additional context around potential threats. By integrating threat intelligence, organizations can proactively identify and block known malicious IPs, domains, or URLs before they even hit their endpoints.
- Security Orchestration and Automation:
Integrating security orchestration and automation tools with Microsoft Defender allows for the creation of automated workflows for incident response. These workflows can be triggered based on specific alerts or events from both Microsoft Defender and other security solutions, enabling faster and more effective response to threats.
Benefits of integrating other security solutions with Microsoft Defender for Endpoint and Advanced Hunting:
- Comprehensive visibility:
Integrating other security solutions with Microsoft Defender provides a more comprehensive view of an organization's environment by combining data from multiple sources. This enables better threat detection and faster response to potential threats.
- Improved threat hunting:
With access to a wider range of data, security teams can conduct more thorough threat hunting activities, uncovering malicious activity that may have gone undetected otherwise.
- Automated response:
By integrating security orchestration and automation tools, organizations can create automated response workflows that speed up incident response times and reduce the risk of human error.
- Cost-effective:
Integrating other security solutions with Microsoft Defender can also be cost-effective as it leverages existing investments in security tools and platforms.
In conclusion, integrating other security solutions with Microsoft Defender for Endpoint and Advanced Hunting can greatly enhance an organization's overall security posture by providing a more comprehensive approach to threat detection, response, and hunting. This integration enables organizations to take advantage of the advanced capabilities of Microsoft's endpoint protection systems while leveraging data from other security tools and platforms.
Conclusion
In this rapidly evolving digital landscape, it is crucial for security teams to have access to the best tools and technology. Microsoft's Defender for Endpoint and 365 Defender offer advanced hunting capabilities that can empower teams to proactively identify and address potential threats. By harnessing these powerful tools, companies can enhance their overall security posture and better protect their valuable data. It is time for organizations to embrace the potential of Microsoft Defender and take a proactive approach towards securing their systems. With continuous advancements in threat detection and response, we can create a safer digital environment together.


