The Proof of Concept (POC) process plays an important part in any digital transformation. It's a great tool for validating and experimenting with new technologies before you commit to them. Microsoft Sentinel is one of the most innovative security threat detection capabilities available today, and its POC can be successful when it's done correctly.
In this blog post, we look at the basics of Microsoft Sentinel and how you can create a successful POC for it. We’ll discuss best practices for creating a secure environment, tools to collect customer feedback, as well as some other helpful tips. Read on to find out more about making sure that your POC runs smoothly using Microsoft Sentinel!
What is a Proof of Concept (POC)?
A Proof of Concept (POC) is an opportunity to evaluate the potential of a proposed solution. Organizations can use it to assess the feasibility of a project and decide if it's worth pursuing. If a POC is successful, it could result in the implementation of the suggested solution.
Microsoft Sentinel is a cloud-native security platform that helps organizations detect, investigate, and respond to threats. To make sure you get the most out of your POC experience with Sentinel, define your goals and objectives beforehand, identify appropriate data sources, and have an action plan for using its features.
Once those steps are done, you can start collecting data and generating alerts to get a deeper insight into your organization's security posture through Sentinel.
Aims and Objectives of a Sentinel POC
The aim of a POC is to test the viability of a project or solution. The objectives of a POC are:
- Demonstrate the feasibility of the proposed solution or project.
- Determine any risks associated with the proposed solution or project.
- Get feedback from stakeholders on the proposed solution or project.
- A POC could be used to gain support for the proposed solution or project.
A comparison with other SIEM services such as Splunk could also be an objective.
How to get started with Microsoft Sentinel
If you're looking to get started with Microsoft Sentinel, there are a few things you'll need to do. To get started, you'll need to create a new Azure workspace and create an Azure account. Afterward, you'll have to add the Sentinel data sources you want to monitor to your workspace. To do this, go to the "Data Connectors" blade within the Azure portal.
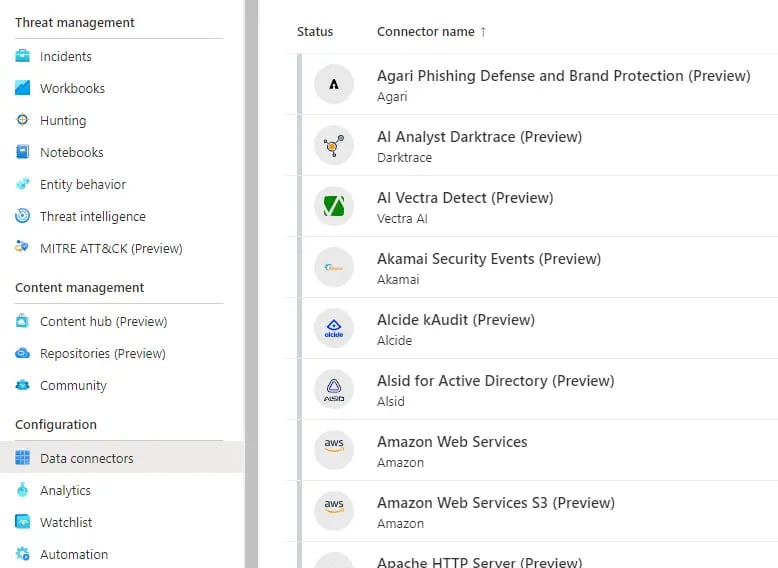
In the Azure portal, you can create custom rules based on the data sources that you've configured by visiting the "Analytics" blade.
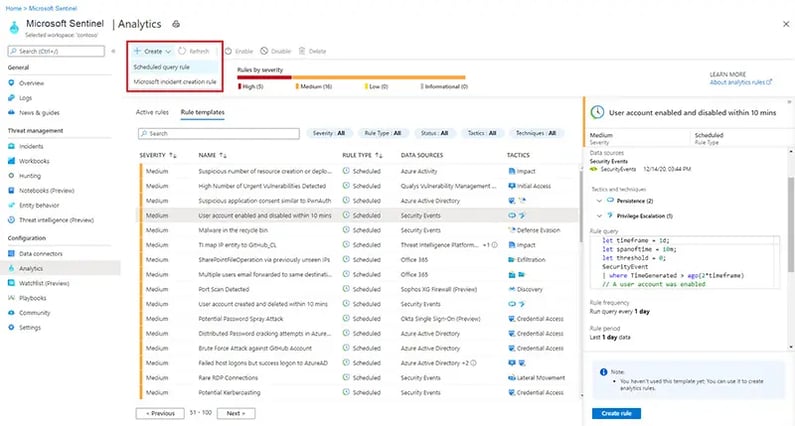
The MITRE ATT&CK framework can be mapped to your rules by adding tags when creating your rules. These tags will help you categorize and search for specific threats. For example, if you wanted to create a rule that alerted on suspicious behavior related to DNS tunneling, you could create a tag called "T1036 - Tunneling" and assign it to the rule. In Microsoft Sentinel, all tunneling rules will be grouped together and easily searchable.
You can conduct deep analysis of your data sources, create custom queries, and gain visibility into emerging and unknown threats using the "Hunting" blade of Microsoft Sentinel.
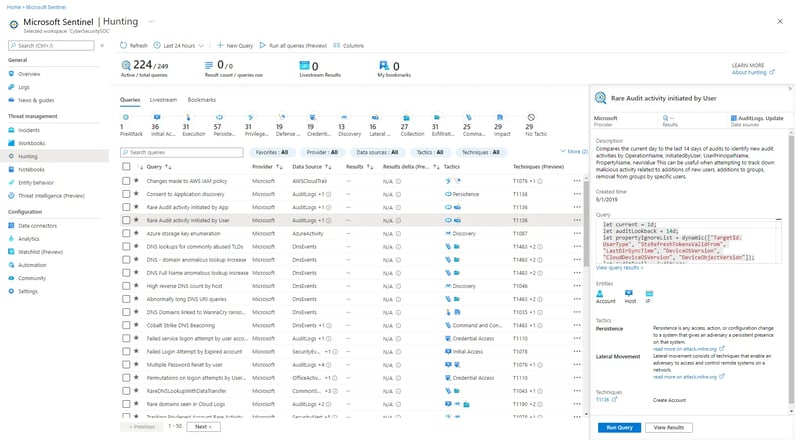
A quick way to find anomalies and correlations across all the data sources you configured in your workspace is through the "Hunting" blade. Additionally, the blade's machine learning algorithms can detect malicious activity automatically and notify you when it is detected. In addition, it offers powerful search capabilities that help you narrow down results and uncover potential threats.
Microsoft Sentinel's "Hunting" blade allows you to identify unknown threats quickly and respond appropriately to them.
In order to detect and respond to threats, Microsoft Sentinel uses internal as well as external threat intelligence. VirusTotal, Microsoft Threat Intelligence Center, and National Security Agency Cyber Threat Framework (CTF) are some of the public sources it can query. You can detect malicious activities and known threats by building Threat Intel into rules.
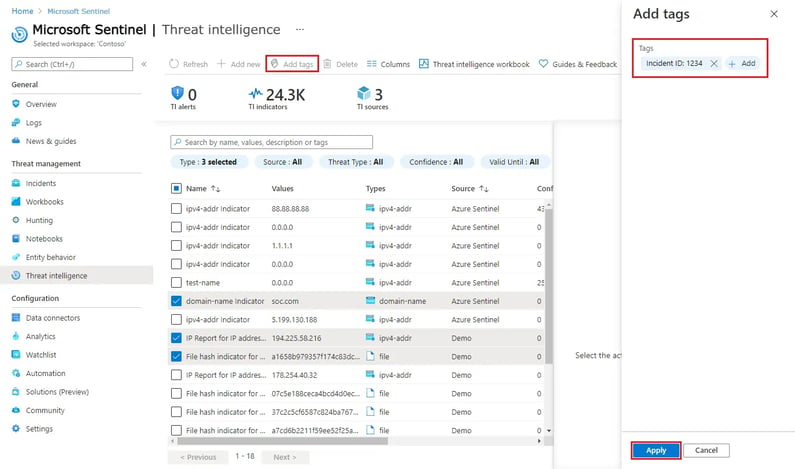
The Microsoft Graph Security API can also be integrated with other security products and solutions in your organization, such as antivirus software and intrusion detection software. As a result, you are able to detect threats more accurately and with a more comprehensive view of them.
Once you have set up your environment, you can begin to track and analyze the security of your organization through the dashboards. You can also personalize your surveillance capabilities by configuring internal or third-party threat intelligence sources. This way, you can guarantee that your organization is guarded against the newest risks.
Microsoft Sentinel continuously monitors these threat intelligence sources once they have been configured. The platform will automatically flag and alert any potential malicious activity when it is detected. As a result, your organization can take action quickly to protect itself from threats.
As a last step, you'll need to set up some alerts in order to be notified when something interesting happens. In the Azure portal, you can configure email and other notification settings to be notified when something goes wrong by going to the "Incident" blade.
The Microsoft Sentinel security platform enables organizations to quickly detect and respond to threats by providing a user-friendly interface that makes it easy to create rules and investigate suspicious activity. The integration of external threat intelligence sources and other security solutions allows for quick identification and response to unknown threats.
Why Use Microsoft Sentinel for Your POC?
Powered by artificial intelligence (AI), Microsoft Sentinel provides proactive and comprehensive data and device protection for your organization.
In addition to providing comprehensive visibility into your organization’s entire ecosystem, including on-premises, hybrid, and cloud environments, Microsoft Sentinel is designed to be easily deployed and integrated into your existing security infrastructure. The Microsoft Sentinel platform also offers advanced threat detection and response capabilities.
In addition to being scalable, easy to deploy, and providing comprehensive visibility into your organization's ecosystem, Microsoft Sentinel is a great platform for Proof of Concept (POC) projects. With Microsoft Sentinel, you can also detect and respond to threats more effectively and quickly thanks to its AI-powered security capabilities.
With its ability to integrate with hundreds of third-party security solutions and compatibility with dozens of operating systems, Microsoft Sentinel is a perfect choice for multi-vendor environments. In addition, it provides automated policy enforcement and simplified alerting, which reduce complexity and increase ease of use.
Microsoft Sentinel provides comprehensive visibility, advanced threat detection, and streamlined response capabilities for your organization's environment as a whole. As a result of its scalability, integration capabilities, and ease of use, it is an ideal platform for forward-thinking security monitoring projects.
How to create a successful POC with Microsoft Sentinel
The following steps will help ensure a successful POC with Microsoft Sentinel:
- Describe the business problem or opportunity you hope to solve with Sentinel. What are your specific goals?
- Identify the Sentinel use cases that are best aligned with your business problem or opportunity. What are the potential benefits of using Sentinel?
- Prepare a detailed plan for how you will test Sentinel in your environment. Which data sources will you use, how will you evaluate results, and what success criteria will you use?
- Implement your plan and collect data on Sentinel's performance. Pay close attention to any areas where Sentinel does not meet your expectations.
- Analyze the results of your POC and determine whether or not to move forward with Sentinel implementation. Communicate your findings and recommendations to key stakeholders.
How to Implement a Successful POC with Microsoft Sentinel
Before making a decision to purchase or roll out a new security solution company-wide, many organizations choose to test whether the solution meets their needs through a Proof of Concept (POC). This blog post provides an overview of how to implement a successful POC with Microsoft Sentinel, which is a cloud-native security information and event management (SIEM) platform that can help organizations detect, investigate, and respond to threats in real time.
The first step is to identify your organization's specific needs and requirements for a SIEM solution. Once you have answers to these questions, you can set up your Azure Sentinel POC environment. What are your goals for using a SIEM? How will you collect and monitor data?
After configuring Azure Sentinel to collect data from the desired data sources, you'll need to set up rules and alerts to monitor for threats. After configuring the data collection, you'll need to set up rules and alerts. For your data to be secure, compliance and data storage should be configured as well.
You can test the Azure Sentinel environment by running simulated scenarios and generating sample alerts. This will allow you to identify potential issues before they become serious.
Last but not least, you'll need to analyze the results of your POC. Was Azure Sentinel able to meet all of your requirements? Could it have been improved or optimized in any way? You will be able to decide whether Azure Sentinel is the right solution for your organization by answering these questions.
Data connectors with Microsoft Sentinel
Sentinel is a cloud-native platform that helps you identify and investigate threats across your entire organization by ingesting, storing, and analyzing large amounts of data in real time.
You can use Microsoft Sentinel to detect and respond to threats more quickly and effectively if you connect it to as many data sources as possible.
With Microsoft Sentinel, you can easily import data from a wide variety of different sources thanks to its built-in connectors. We'll take a look at some of Microsoft Sentinel's most popular data connectors in this blog post and see how they can improve your security.
The first connector we will examine is the Office 365 connector. This connector allows you to ingest data from all sorts of Office 365 services, including Exchange Online, SharePoint Online, Azure Active Directory, and more. For detecting suspicious activity, such as anomalous login attempts or malware-laden emails, this data can be extremely valuable.
Windows Event Log connectors are another popular connector. With this connector, you can import data from your servers and workstations' event logs. This data can be used to detect a wide range of malicious activity, including brute force attacks, malware infections, and unauthorized system changes.
Other built-in connectors for Microsoft Sentinel include Syslog, Defender for Cloud, Microsoft 365 Defender, and Amazon Web Services. Additionally, there is a range of third-party connectors that can be used to ingest data from all sorts of other sources, such as cloud applications, network devices, and security solutions.
Connecting Microsoft Sentinel to as many data sources as possible will enable you to get a comprehensive view of your environment to detect and respond to threats quickly.
Best Practices for Your POC Implementation
You should keep a few best practices in mind when implementing a Proof of Concept (POC) in Microsoft Sentinel. It’s crucial that you set a clear, concise goal for your POC. What are you hoping to accomplish with Sentinel? Once you know your goal, you can create an attack plan that will help you achieve it.
It's also important to understand how Sentinel works and how the different components work together. The platform is comprised of several different services, each of which offers unique capabilities. You can achieve your POC goals more effectively by first understanding the capabilities within Sentinel.
Your team can also become more comfortable with Sentinel by running it alongside Splunk or other SIEMs. Moreover, by doing so, you will gain a better understanding of how Sentinel works in relation to other tools and how it can be used to enhance your security posture. Additionally, Microsoft has rich features for Threat Hunting enabling you to dig deeper into your data.
The process of detecting threats in Microsoft Sentinel is complex, so understanding and utilizing these best practices can help you make the most of your POC. You can successfully implement a Microsoft Sentinel proof of concept if you understand how to use Sentinel effectively and involve your team in the process.
Follow these best practices when implementing a POC for Microsoft Sentinel and you'll be well on your way to achieving your goals.
Lastly, ensure that your Sentinel POC has the right resources in place. This includes IT, security, and operations personnel, as well as other stakeholders who can contribute to the project's success. If you have the right team of people working together on the same goal, the implementation will run more smoothly and be more successful.
Conclusion
Microsoft Sentinel is an effective way for businesses to manage and secure their data. Equipped with a user-friendly interface, AI features and automated operations, it helps organizations identify potential risks quickly. To make the right choice when selecting a security system for your company, it's important to understand the importance of a successful Proof of Concept (POC) process.
Quzara LLC has successful experience with providing companies with guidance and support before, during, and after the POC process, so you can be confident that Microsoft Sentinel will be the suitable solution for your business needs.
For more information visit quzara.com/sentinelpoc

