Introduction to Threat Hunting
Unleashing the power of threat hunting is a game-changer in today's fast-paced digital landscape. As cyber threats continue to evolve and become more sophisticated, organizations must stay one step ahead to protect their sensitive data and infrastructure. That's where innovative solutions like Microsoft Sentinel and Splunk Enterprise Security come into play.
In this blog post, we will dive deep into the world of threat hunting and explore the key differences between Microsoft Sentinel and Splunk Enterprise Security. Both platforms offer robust capabilities for detecting, analyzing, and mitigating security incidents. So, buckle up as we embark on an exciting journey through these cutting-edge tools that leverage big data hunting, advanced rules, automation, and much more!
Whether you're new to threat hunting or looking to enhance your existing capabilities, this blog post has got you covered. So, let's get started on our quest to find the perfect solution for your organization!
Microsoft Sentinel vs Splunk Enterprise Security
Microsoft Sentinel and Splunk Enterprise Security are two leading solutions in the field of threat hunting. Both platforms offer powerful features and capabilities that enable organizations to proactively detect, investigate, and respond to potential security threats.
When it comes to threat hunting, Microsoft Sentinel stands out with its integration with the Mitre ATT&CK framework. This allows security teams to map observed behaviors against known attack techniques, providing valuable insights into potential threats. Additionally, Microsoft Sentinel leverages advanced hunting rules that enable analysts to create custom queries based on specific indicators or patterns of activity.
On the other hand, Splunk Enterprise Security excels in its ability to handle big data hunting. With its robust log collection and analysis capabilities, organizations can ingest vast amounts of data from various sources and uncover hidden threats or anomalies. Moreover, Splunk's automated response workflows (SOAR) enhance efficiency by automating repetitive tasks.
In terms of user interface, both platforms offer intuitive dashboards and visualizations that make it easy for analysts to identify potential threats quickly. However, each platform has its own unique layout and design elements that may appeal differently depending on individual preferences.
When it comes to threat hunting, the decision between Microsoft Sentinel and Splunk Enterprise Security ultimately depends on the unique needs and requirements of an organization. Each solution has its own strengths in various areas, such as integration with the Mitre ATT&CK framework or handling big data hunting.
What are the Key Features of Microsoft Sentinel and Splunk Enterprise Security for Threat Hunting?
Microsoft Sentinel and Splunk Enterprise Security are both powerful tools that offer robust features for threat hunting. Let's take a closer look at some key features provided by each platform.
Microsoft Sentinel, an intelligent security analytics solution, leverages the power of cloud computing to enable effective threat detection and response. It harnesses machine learning algorithms and advanced analytics capabilities to identify potential threats in real-time. With its integration with the Mitre ATT&CK framework, it provides comprehensive coverage across different attack vectors.
On the other hand, Splunk Enterprise Security is renowned for its ability to process vast amounts of data quickly. This makes it ideal for big data hunting, where analysts need to sift through massive volumes of log files and events to uncover hidden threats. Its correlation search feature allows users to detect patterns and anomalies in data, enabling proactive threat hunting.
Both platforms also offer advanced hunting rules that allow security teams to create custom queries tailored to their specific environment. This flexibility enables organizations to adapt their threat hunting strategies based on evolving threats.
Additionally, Microsoft Sentinel offers built-in SOAR (Security Orchestration Automation Response) capabilities which help automate incident response actions based on predefined playbooks. This streamlines the remediation process and reduces manual intervention required during incident handling.
In comparison, Splunk Enterprise Security provides a user-friendly interface with customizable dashboards that provide visibility into critical security events at a glance. These dashboards can be tailored according to individual preferences or organizational requirements.
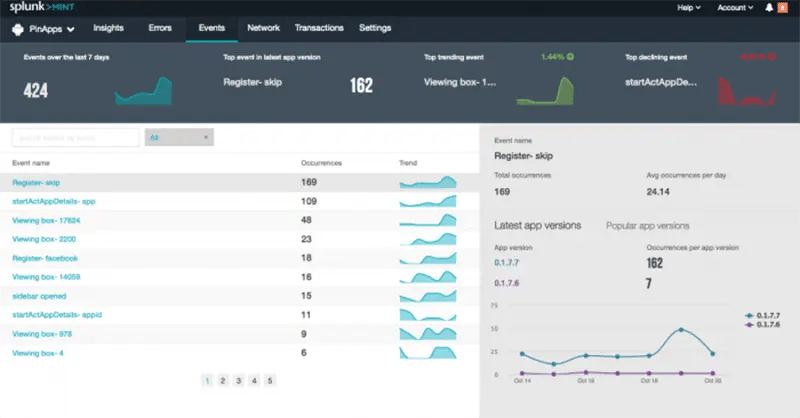
While both Microsoft Sentinel and Splunk Enterprise Security offer powerful features for threat hunting, they have distinct strengths that cater to different needs. Organizations must carefully evaluate their specific requirements before choosing the right solution for efficient threat detection and response.
What are the Threat Hunting Use Cases for Microsoft Sentinel and Splunk Enterprise Security?
Microsoft Sentinel and Splunk Enterprise Security are both powerful tools when it comes to threat hunting. They provide security teams with the ability to proactively detect and respond to potential threats in their networks. Let's explore some of the use cases where these platforms excel.
One common use case for threat hunting is leveraging the Mitre ATT&CK framework. Both Microsoft Sentinel and Splunk Enterprise Security offer support for this industry-standard framework, allowing security analysts to map observed behaviors against known attack techniques. This enables them to identify any suspicious activities that might indicate a potential compromise.
Another important aspect of threat hunting is Big Data hunting. With vast amounts of data being generated every day, it can be challenging to sift through all the noise and find meaningful insights. This is where advanced analytics capabilities provided by both platforms come into play. Analysts can leverage these capabilities to search, filter, and correlate large volumes of data in real-time, identifying patterns or anomalies that may indicate malicious activity.
Automation is another key feature offered by both platforms that significantly enhances the efficiency of threat hunting operations. By automating tasks such as log collection, analysis, and response actions, security teams can focus on investigating more complex threats rather than getting bogged down with manual processes.
Both Microsoft Sentinel and Splunk Enterprise Security also integrate seamlessly with SOAR (Security Orchestration Automation Response) solutions. This allows organizations to streamline their incident response workflows by automating repetitive tasks like alert triage or containment actions.
Whether you choose Microsoft Sentinel or Splunk Enterprise Security for your threat hunting needs depends on various factors such as budgetary constraints or existing infrastructure considerations. However, what's clear is that both platforms offer robust features designed specifically for proactive detection of threats in today's rapidly evolving cybersecurity landscape.
User Interface Comparison
Microsoft Sentinel and Splunk Enterprise Security have different user interfaces when it comes to threat hunting. Let's take a closer look at how they compare.
Microsoft Sentinel offers a clean and intuitive interface that is designed with simplicity in mind. The dashboard provides an overview of your security posture, allowing you to quickly identify any potential threats. Navigating through the various tabs and menus is straightforward, making it easy for even novice users to navigate.
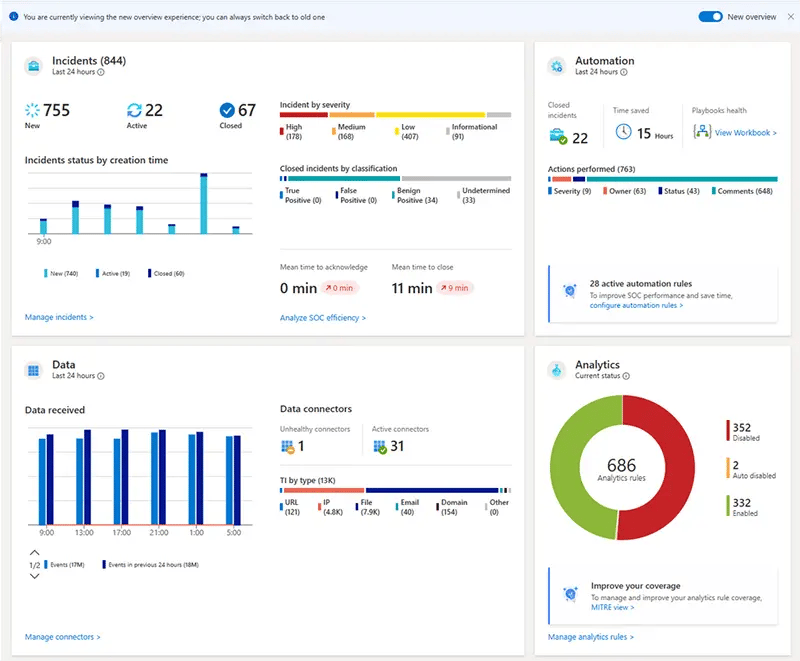
On the other hand, Splunk Enterprise Security has a more complex user interface that may require some time and training to fully understand. It offers extensive customization options, allowing users to tailor the interface according to their specific needs. However, this flexibility can also make it overwhelming for those who are not familiar with the platform.
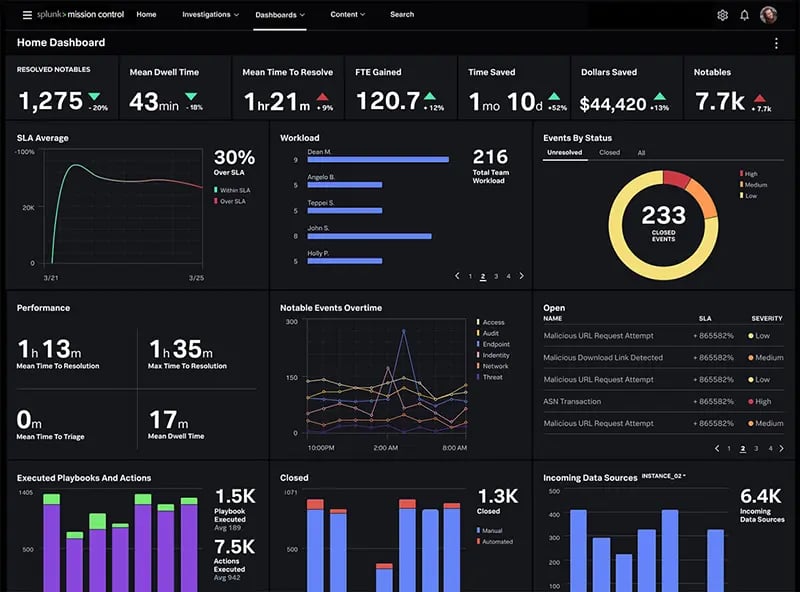
In terms of visualization capabilities, both platforms offer powerful tools for displaying data in meaningful ways. Microsoft Sentinel provides pre-built visualizations that are easy to interpret at a glance. Splunk Enterprise Security allows for advanced customization of dashboards and reports, providing more flexibility but also requiring additional expertise.
Choosing between Microsoft Sentinel and Splunk Enterprise Security will largely depend on your team's familiarity with each platform and their specific requirements regarding user experience.
Conclusion: Choosing the Right Threat Hunting Solution
When it comes to threat hunting, both Microsoft Sentinel and Splunk Enterprise Security offer robust solutions that can help organizations stay ahead of cyber threats. While they have some similarities, there are also key differences that set them apart.
Microsoft Sentinel is a cloud-native SIEM solution that leverages the power of AI and machine learning to detect and respond to threats in real-time. With its integration with Azure services and built-in automation capabilities, it provides a comprehensive approach to threat hunting. It also aligns well with the Mitre ATT&CK framework, making it easier for security teams to map their detection rules against known adversary techniques.
On the other hand, Splunk Enterprise Security offers a powerful big data platform combined with advanced analytics capabilities. With its flexible architecture and extensive customization options, organizations can tailor their threat hunting workflows according to their unique requirements. Splunk's Adaptive Response feature allows for seamless integration with third-party tools, enabling SOC teams to automate incident response actions through SOAR platforms.
When choosing between Microsoft Sentinel and Splunk Enterprise Security for threat hunting, consider factors such as your organization's size, budget constraints, existing infrastructure, and specific use cases. Both solutions have their strengths and weaknesses depending on your needs.
It is important to evaluate your organization's requirements thoroughly before making a decision. Consider factors such as ease of use, scalability potential, and support offerings from vendors when selecting the right solution.
Ultimately, the key to successful threat hunting lies in the ability to access real-time, accurate data insights, and harness advanced automation capabilities for efficient incident response. By combining these elements, organizations can effectively stay ahead of cyber threats and protect their networks from potential compromises.
In the end, the decision on whether to go with Microsoft Sentinel or Splunk Enterprise Security will be influenced by several factors, including:
- Organizational Preferences
- Infrastructure Compatibility
- Budget Considerations
- Specific Use Cases
Whichever solution you choose, remember that effective threat hunting requires:
- Continuous Monitoring
- Adaptability
- Staying up-to-date with Evolving Cyber Threats
Quzara CybertorchTM offers a direct, 24/7 SOC-as-a-Service that aligns with FedRAMP High baseline, delivering around-the-clock threat hunting and incident response. Our service is designed for entities requiring the highest level of data protection and operational continuity. Discover additional information about our solutions on our MXDR page.
For a detailed comparison of Microsoft Sentinel and Splunk, delve into our comprehensive blog. Uncover key differences and similarities in these potent threat hunting solutions to make an informed decision for your organization's security requirements.


