Threat Intelligence is a critical element of any security team's operations, particularly in the digital world. Microsoft Sentinel is amongst the most common Threat Intelligence platforms that provide organizations with total security visibility.
Despite its advantages, it has certain shortcomings that this blog post delves into by discussing how to take advantage of other tools to strengthen your overall security strategy. Keep reading to discover how you can make sure your organization is shielded from emerging cyber threats.
What is Threat Intelligence?
An understanding and anticipation of cyber security threats can be improved with Threat Intelligence (TI). TI includes information about current and emerging threats, as well as potential impacts. TI can be used to help organizations protect themselves from attacks in an informed manner.
It includes a Threat Intelligence service that provides users with information about current and emerging threats. Microsoft Sentinel is a cloud-based SIEM that uses machine learning to detect and investigate security threats. In addition, Microsoft offers a Threat Intelligence API to enable organizations to access third-party Threat Intelligence data.
Organizations can use Threat Intelligence to improve their security posture in several ways. As an example, they can use it to identify high-priority targets for security monitoring and incident response or develop better detection rules and responses. Additionally, TI can aid organizations in preventing attacks by helping them understand the motives and methods of attackers.
The benefits of Threat Intelligence
A key component of Microsoft Sentinel is Threat Intelligence, which helps organizations detect, investigate, and respond to threats. An organization can take proactive measures to defend itself against potential threats by analyzing data from various sources to identify trends, indicators of compromise, and attacker techniques.
Organizations can benefit from Threat Intelligence in a number of ways:
- Through the analysis of data from a variety of sources, Threat Intelligence can identify new and emerging threats, allowing organizations to be proactive instead of waiting for an attack.
- Identifying the cause of an incident: Threat Intelligence can assist investigators in finding the needle in the haystack. Investigators can identify an incident's root cause more quickly and accurately when they have insight into trends and attacker techniques.
- Organizations can craft more effective responses to incidents with Threat Intelligence.
- Organizations can develop better countermeasures and strategies for dealing with incidents by understanding the tactics, techniques, and procedures used by attackers.
- Any organization looking to improve its security posture can benefit from Threat Intelligence. Microsoft Sentinel provides a robust platform for gathering and analyzing threat data, which helps organizations make better security decisions.
How to get started with Microsoft Sentinel
You'll need to do a few things first if you want to start using Microsoft Sentinel. To enable the Sentinel service within the Azure portal, you must first sign up for a free Azure account. Once you have a free Azure account, you can begin using it right away.
Once you have enabled the Sentinel service, you can start ingesting data into Sentinel. There are many ways to do this, but the easiest way is to use one of the built-in connectors. Data can be imported from a variety of sources, including on-premises systems and cloud-based services, using these connectors.
Once you have data flowing into Sentinel, you can start creating queries and alerts based on that data. Queries allow you to explore your data and look for specific patterns, while alerts notify you when certain conditions are met. Playbooks can be created to automate actions when certain situations occur.
Microsoft Sentinel provides a powerful platform for detecting and responding to threats, and it's easy to set up.
Using Threat Intelligence for Microsoft Defender XDR
In addition to providing visibility into and protection against malware, ransomware, and other threats, Microsoft Defender XDR is a cloud-based security solution. You can investigate and respond to incidents more quickly and effectively with Defender XDR integration with Microsoft Sentinel.
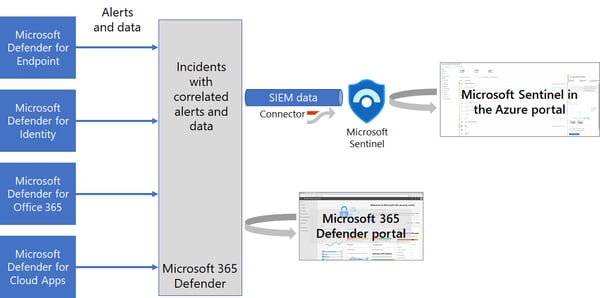
The following topics will be covered in this blog post to help you better understand and defend against threats:
- The Benefits of Using Threat Intelligence in Microsoft Defender XDR
- How to Access and Use Threat Intelligence in Microsoft Defender XDR
- How to Leverage Threat Intelligence to Investigate and Respond to Incidents
The Benefits of Using Threat Intelligence in Microsoft Defender XDR
The use of Threat Intelligence in Microsoft Defender XDR offers a range of advantages for your organization. Through the use of Threat Intelligence, it is possible to identify malicious activity quickly and respond before it can do major damage or disruption. It also provides context about suspicious activity, resulting in fewer false positives. In addition, it allows you to gain a better understanding of techniques used by attackers, enabling you to implement more successful preventative measures for your organization.
How to Access and Use Threat Intelligence in Microsoft Defender XDR
From the top menu bar of Microsoft Defender XDR, select “Threat Analytics” to access and use Threat Intelligence. Select or search for threat from the list in the middle of the page. Also, you can customize alerts it sends you based on the types of security events you want to be informed about.
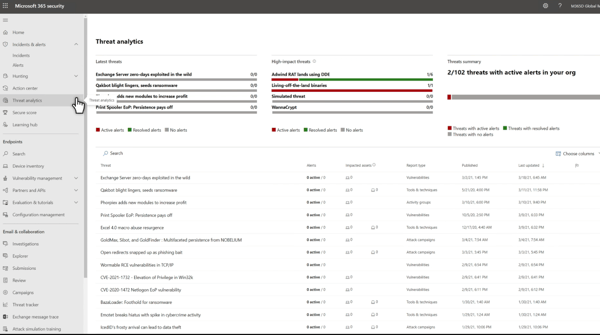
How to Leverage Threat Intelligence to Investigate and Respond to Incidents
When delving into security incidents, Threat Intelligence can be a very useful asset. For example, if you find an odd file on your endpoints, it can help you establish if it is linked with any recognized threats. Furthermore, it can also detect any malicious activities that traditional security measures may have overlooked. With this extra information, you can swiftly investigate and tackle incidents before they lead to severe destruction or disruption for your company.
To access this data within Microsoft Defender XDR, simply go to the Dashboard tab on the left side of the screen, then click on “Threat Analytics"
- How to Use Threat Intelligence in Microsoft Defender XDR
- Threat Intelligence Resources for Microsoft Defender XDR Users
Using Threat Intelligence in Microsoft Defender XDR can assist organizations in quickly identifying and responding to potential threats. By connecting data from Defender for Endpoint, Defender for Cloud, Microsoft Defender Advanced Threat Protection (ATP), Microsoft Defender Research, or third-party sources such as Anomali or Recorded Future, valuable information about possible security issues can be obtained and used to determine the best use of resources. In addition, queries in MDE make it possible to rapidly search through large datasets based on keywords or expressions. Finally, custom playbooks can be devised to automatically take action when certain incidents are encountered multiple times across multiple devices or users within an organization.
Using keywords or phrases, you can filter through vast amounts of data quickly using Microsoft Sentinel's query capabilities. Microsoft Defender for Endpoint also lets you create custom playbooks if certain types of incidents occur repeatedly across multiple devices or users within your organization.
Microsoft Security Graph
With Microsoft Security Graph, organizations can protect their assets using big data and machine learning. In addition to providing a real-time view of global security landscapes, it helps organizations identify, investigate, and respond to threats quickly.
With Security Graph, organizations can analyze large volumes of data to detect anomalies and gain insight into their security posture. In addition to identifying malicious activities, malicious files, and suspicious activity patterns, the service also provides guidance on addressing threats and reducing the likelihood of being compromised again.
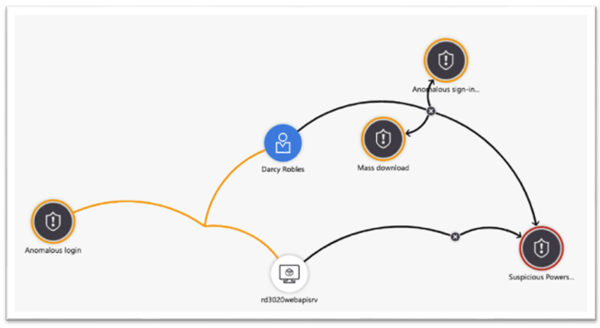
Other platforms for Threat Intelligence
In addition to Microsoft Defender XDR and Advanced Threat Protection (ATP) there are other platforms that provide Threat Intelligence. These include:
- ThreatConnect
- Anomali
- CrowdStrike Falcon Intelligence
- FireEye iSIGHT Intelligence
To find the right platform for your needs, you need to consider its strengths and weaknesses. For example, ThreatConnect offers a robust suite of tools for managing and analyzing data. CrowdStrike Falcon Intelligence provides real-time updates on the latest threats, while Anomali offers detailed threat analysis.
The Benefits of Microsoft Sentinel for Threat Intelligence
Microsoft Sentinel is a cloud-native platform that helps you detect, investigate, and respond to threats. It enables you to procure, analyze, and act on Threat Intelligence so you can better protect your organization.
The benefits of Microsoft Sentinel for Threat Intelligence are many and include the following:
- It helps you collect data from a variety of sources, including Office 365, Azure Active Directory, Cloud Defender, and more.
- It uses artificial intelligence (AI) to help you identify anomalies and potential threats.
- It provides a centralized dashboard where you can view all your security data in one place.
- It offers built-in connectors that make it easy to integrate with other security tools.
- It includes a query language that lets you easily create custom queries to find the specific information you need.
Conclusion
Microsoft Sentinel offers an essential tool for consuming Threat Intelligence by integrating Microsoft Defender XDR as well as AI and machine learning to quickly detect risks. There are various third-party systems that can add on to the abilities of Sentinel to further secure organizations. Having the ideal Threat Intelligence and monitoring systems in place gives businesses the assurance they need regarding their security.
Quzara enables organizations to provide XMDR services with the integration of Microsoft, Open-source, and third party Threat Intelligence into sentinel. This allows for streamlined data collection from a variety of sources and provides analysts with a comprehensive view of an organization's threat landscape. Additionally, Quzara's XMDR services can be customized to meet the specific needs of an organization, making it an ideal solution for businesses of all sizes. Contact us for more information.


