Cyber Threat Intelligence Informs the Security Posture
The broad and ever-increasing adoption of digital technology for vital government, public, and private operations has given rise to a parallel, often sophisticated, and constantly evolving, exploitative culture composed of nation-state sponsored and transnational Advanced Persistent Threats (APT), cybercriminals, and hacktivist groups.
Now more than ever Cyber Threat Intelligence (CTI) is imperative for organizations to accurately understand their risks from threats to existing technologies and processes including interconnections with vendors, partners, and other third parties.
A tailored CTI program provides the intelligence information and assessments that leaders and security teams require to understand the threat landscape and make informed decisions on their incident response approach, monitoring operations, vulnerability management, security policies, and overall security posture.
Specifically, CTI can provide focused information on Threat Actor behaviors, exploits, tools and techniques, an organization's external attack surface, actively targeted vulnerabilities, trends, and emerging threats.
Cyber Threat Intelligence touches all areas of the overall security program and spills over into other areas of the business as well. Figure 1 shows where CTI typically resides within an organization.
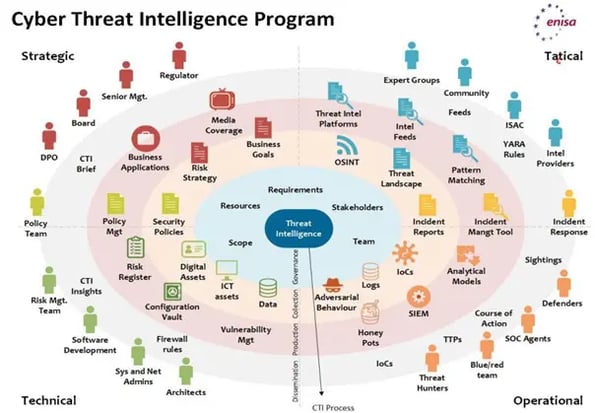
Importance of a Cyber Threat Intelligence Program
A Threat Intelligence Program is imperative for an organization’s success in cyber protection, like that of the “business intelligence” function that informs on market and competitor activities, but from a security threats perspective.
The first step in developing an effective Threat Intelligence Program is determining the specific risks to the organization centered on technology, information, people, and processes.
Second, determining how threat intelligence can assist in addressing the risks to obtain the desired results.
Third, from the findings determine the technology, information, processes, and people required to obtain and act on the Threat Intelligence aligned with the identified risks.
This is important in identifying your organization’s intelligence information requirements and the appropriate combination of sources, feeds, tools, vendors, and third parties to obtain the necessary intelligence aligned with the organization’s intelligence information requirements.
Groups within the security operations purview will benefit from Threat Intelligence with more informed decision making in general, prioritization of vulnerabilities, monitoring and detection operations, incident response, and external attack surface threat awareness.
A couple of quick wins for an organization is to use Threat Intelligence to inform the prioritization of vulnerability management efforts. This is done by identifying known exploited vulnerabilities from the often-sizable list of vulnerabilities for the organization to address and review threat trends specific to the business sector to inform security posture decisions.
Figure 2 outlines multiple security groups with an example Threat Intelligence benefit for each.
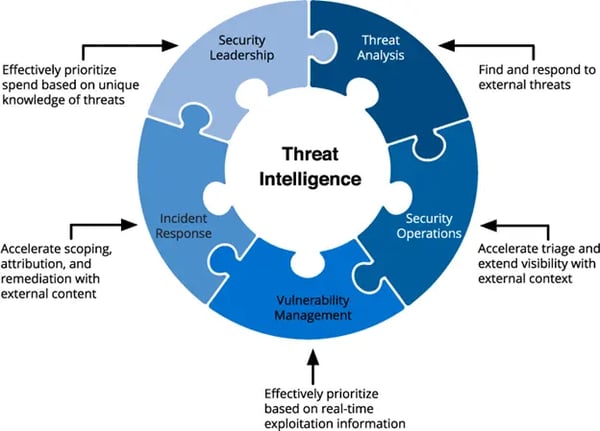
Cyber Threat Intelligence Explained
Threat intelligence information is typically collected in large volumes of raw data from many differing external sources across the clear, deep, and dark webs and internally from security tools, hunting, and investigations.
Examples of external sources include paste sites, black markets, illicit forums, messaging platforms, discussion boards, social media, focused searches across differing search engines, media outlets, niche datasets queried through APIs and web forms, crowdsourced reputation collections, threat actor engagements, open-source threat indicator collections, and scanning or sniffing tools.
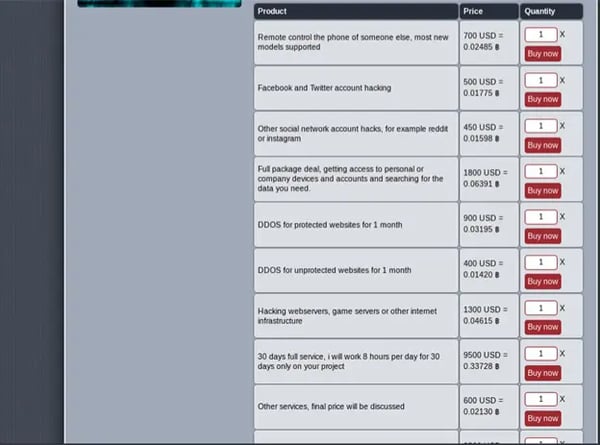
Figure 3 shows an example of a “Hacker-for-Hire" listing on the Dark Web. The rate for hacking a web server is listed at 1300.00 USD.
Examples of internal sources include email phishing protection tools, network and endpoint intrusion detection and prevention tools, Data Loss Prevention (DLP) tools, Security Information and Event Management (SIEM), anomalous activity and incident investigations, threat hunting for indicators of attack, denial & deception technology, and malware analysis.
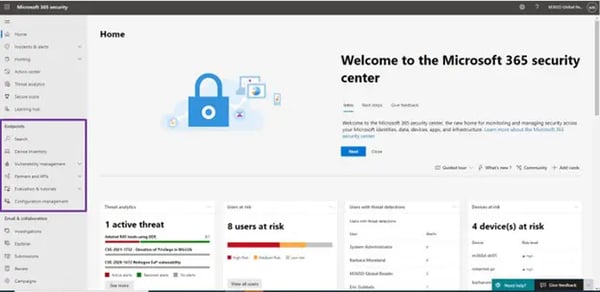
Figure 4 shows a view of the Microsoft 365 Defender Security Center that acts as the single-pane-of-glass.
Commercial and open-source solutions are available to collect, combine, and assist in finding relationships among the multi-source intelligence information analyzed through data science techniques, e.g., Machine Learning (ML) and Artificial Intelligence (AI).
This assists in understanding threat trends and associations, including attribution of threat actors related to identified attack indicators and artifacts together with tactics and techniques.
Figure 5 shows an example of a Threat Intelligence dashboard used to maintain general awareness of threat trends.
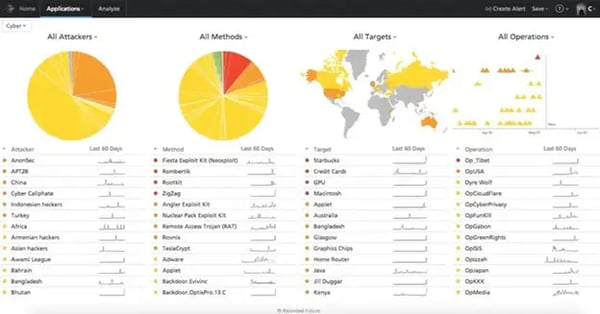
Although AI and machine learning can currently improve the effectiveness and speed of Threat Intelligence fusion, the review of unstructured (as well as structured) data necessary to assess threat information credibility requires a human in the loop.
Later in this article a new OpenAI capability by Microsoft called “Security Co-Pilot” will be presented. Security Co-Pilot helps bridge the supply and demand gap of skilled cyber security professionals.
Leveraging the Microsoft Threat Intelligence Stack
An effective Threat Intelligence Stack leverages signals from the internal security stack and integrates external information which is typically all fed into the Security Information and Event Monitoring (SIEM) system.
Many organizations have a diverse set of internal security tools from various vendors which often creates integration headaches and increased costs over time.
Microsoft continues to increase its internal security offerings and has consolidated these into the Microsoft 365 Defender for easy integration toward single-pane-of-glass.
The security areas now covered include endpoints, Office 365, identity protection, cloud applications, vulnerability management, data loss prevention, and application governance.
The external Threat Intelligence offerings have also expanded with Microsoft Defender for Threat Intelligence (MDTI), Microsoft External Attack Surface Management (EASM), and ChatGPT (aka Co-Pilot).
Together, these offerings provide organizations with an understanding of their external footprint and related vulnerabilities.
These also assist security operations with an evaluation of internal events with external intelligence enrichment and threat awareness.
To augment the Threat Intelligence Stack further combine it with open source and commercial Intelligence feeds, Dark Web Intelligence Providers, additional Threat Research publications, and additional media and government reporting.
Consolidating internal and external signals and feeding them into the Azure Sentinel SIEM and back into the internal security tools, where applicable, completes the stack where the bulk of the alerting, hunting, and anomaly detection takes place with easy integration to Microsoft Defender, MDTI, Security Copilot, and EASM.
Figure 6 depicts the general Internal and External Threat Intelligence Stack with a Microsoft and security operations focus.
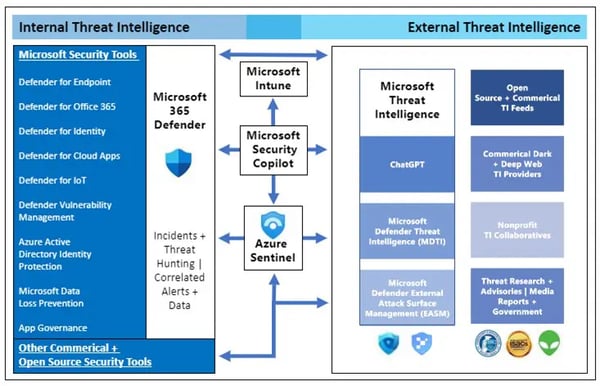
Microsoft Defender Threat Intelligence (MDTI)
Microsoft Defender for Threat Intelligence collects, analyzes, and indexes open-source information to assist organizations in detecting and responding to threats, prioritizing incidents, and proactively identifying threats targeting their assets.
Microsoft collects internet data with their Protective DNS sensor network, global proxy collection of virtual users, port scans, and third-party sources for malware and added Domain Name System (DNS) information.
Collection is split into two areas including traditional and advanced. Traditional includes:
- Resolutions
- WHOIS
- SSL Certificates
- Subdomains
- DNS
- Reverse DNS
- Services
Advanced includes:
- Trackers
- Components
- Host Pairs
- Cookies
Trackers, Components, Host Pairs, and Cookies data sets are collected from the webpage Document Object Model (DOM).
Additionally, Components and Trackers are observed from detection rules that trigger banner responses from port scans or SSL Certificate information.
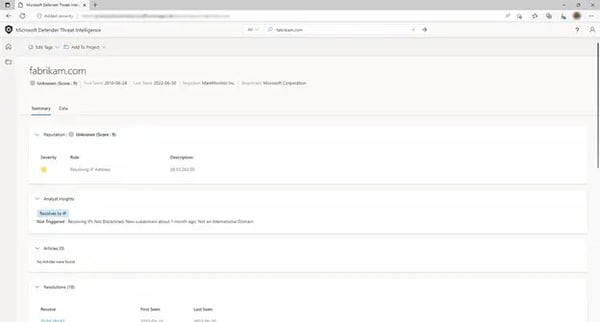
Figure 7 shows an example of the traditional and advanced information collection from an IP investigation with MDTI.
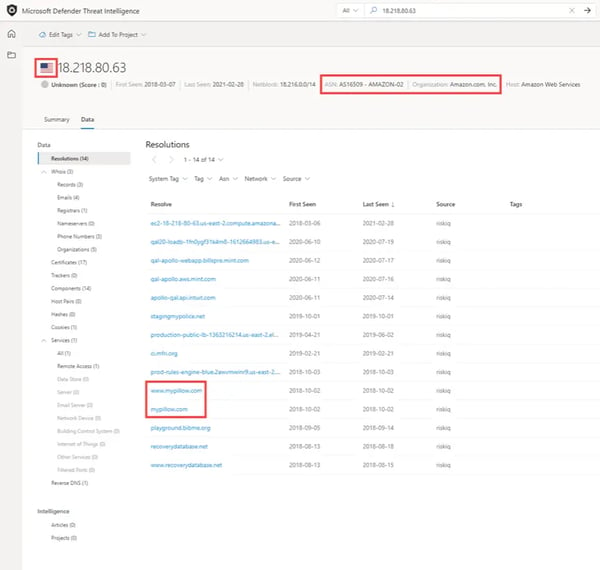
MDTI also maintains Public and Microsoft curated Indicators, vulnerability, and threat articles, as well as host, domain, and IP address reputation scoring. Recent development includes threat actor and campaign attribution via a paid service.
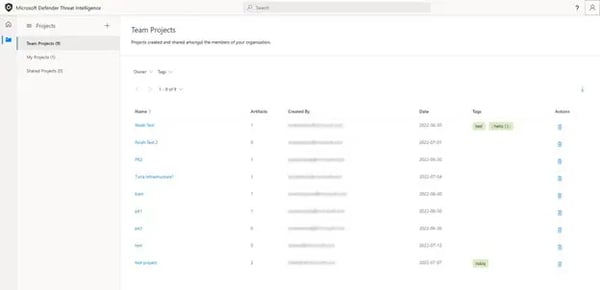
MDTI goes beyond intelligence information collection with the project and analyst insights capabilities. Teams can deploy projects to collaborate on threats during internal and external investigations (see Figure 8 for Team Projects View).
Analyst insights are a curated handful of observations that increase the effectiveness of an investigation and make it more intelligible to analysts of all skill levels.
Insights includes information on domain or IP address that provides Defender TI users with the ability to make an assessment on the signal or information queried to improve an analyst's ability to determine if an indicator is malicious, suspicious, or benign (see Figure 9, Analysts Insights Example).
Microsoft Defender External Attack Surface Management (EASM)
Defender EASM is a paid service that applies web crawling to discover externally facing assets and actively scans them to discover related attributes and new connections over time. Attack Surface awareness is created by collecting and evaluating vulnerability and infrastructure data to identify key areas of concern for an organization to include:
- Discover digital assets continuously
- Analyze and prioritize risks and threats
- Detect externally exposed weaknesses on demand and from any place
- Gain third-party attack surfaces visibility
EASM collects data for publicly exposed assets and can be coupled with Defender for Cloud CSPM to assist with inside-out asset exposure validation to provide increased asset visibility.
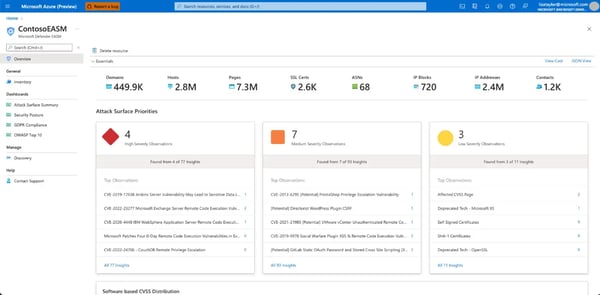
Figure 10 shows an EASM overview with a summary of external vulnerabilities detected.
Defender EASM includes the discovery of the following types of assets:
- Domains
- Hostnames
- Web Pages
- IP Blocks
- IP Addresses
- ASNs
- SSL Certificates
- WHOIS Contacts
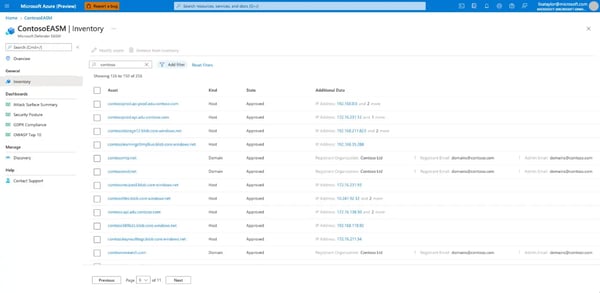
EASM looks for these types of externally facing assets that are exposed to the open internet beyond traditional firewall protection (see Figure 11, EASM Inventory Listing Example).
Microsoft 365 Defender
Microsoft 365 Defender brings together the following into a single-pane-of-glass:
- Defender for Endpoint
- Office 365
- Identity
- Cloud
- Vulnerability Management
- Data Loss Prevention
- IoT
- App Governance
This together with hunting, detection alerting, and incident capabilities provides for a cross-product awareness of:
- Internal threats, risks, and attacks
- Reduce signal noise with data matching
- Auto healing of affected assets
- Combined incidents queue
- Automatic response to threats
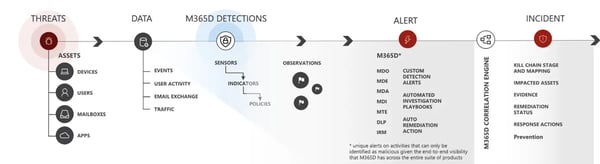
Microsoft 365 Defender takes signals from devices, applications, users, and systems watching for indicators of attack. If indicators are observed alerts are created and evaluated for incident status (see Figure 12, Microsoft 365 Defender Flow).
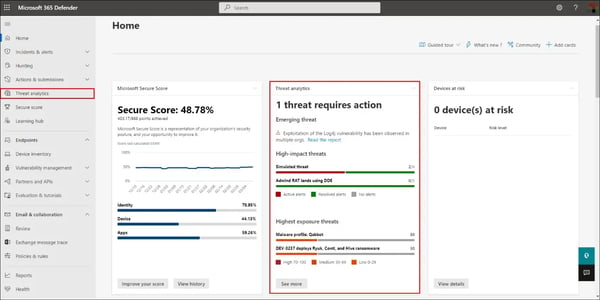
Two key Threat Intelligence features of Defender include Threat Analytics and Advanced Threat Hunting. Threat Analytics is used to track prevalent threats and those making the news. Microsoft 365 Defender Threat Analytics assists organizations in the following areas:
- Detailed analyst reports created by Microsoft security research into recently surfaced vulnerabilities, threat actors, and their campaigns with a paid subscription. The reports also contain detailed information on how to remediate.
- Information on how the identified threats is applicable to your environment.
Reviewing and responding to incidents and leveraging advanced hunting are likely daily tasks for security groups and the Threat Analytics feature will assist in these tasks.
See Figure 13 for a view of the Threat Analytics Dashboard.
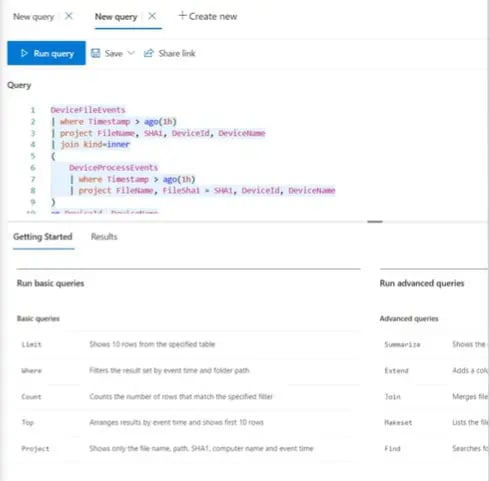
Advanced Threat hunting allows organizations to leverage their unique environmental knowledge to hunt indicators of attack with the creation of custom queries to leverage the raw data collected by the various security products.
See Figure 14 for an Advanced Threat Hunting Example. Microsoft 365 Defender provides query-based access to 30-days of historic raw data for end point and Office 365.
An added benefit to the single-pane-of-glass is the ability to send the collected signals, alerts, and incidents to a SIEM including Microsoft and Azure Sentinel to enable additional cross-domain threat and incident alerting awareness.
This data may also be sent to other systems or data stores for additional evaluation and enrichment before going into Sentinel for added value through the lowering of false-positive rates.
Microsoft Sentinel
Sentinel acts as the central hub for logging, consolidating, and assessing signals and alerts from Microsoft Defender and other security tools. It also has built-in entity behavioral analytics and machine learning.
Sentinel can also integrate the MDTI threat feed, other Threat Intelligence feeds from commercial and open-source offerings for hunting, alerting, playbook, and incidents support (see Figure 15, Sentinel Threat Intelligence Integration Flow).
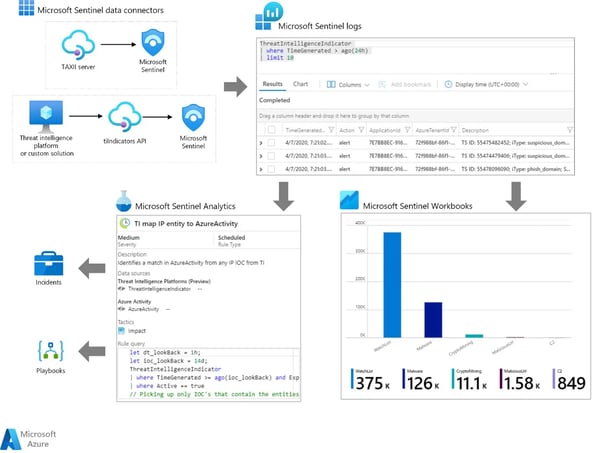
Threat intelligence integration with Microsoft Sentinel involves the following:
- Import threat intelligence through data connectors for various Threat feeds and providers.
- View and manage imported threat intelligence to Sentinel (see Figure 16, Sentinel Threat Intelligence Blade).
- Apply built-in analytic rules to detect threats and create alerts and incidents from the imported threat intelligence.
- Visualize key information on imported threat intelligence to Microsoft Sentinel with the Threat Intelligence workbook.
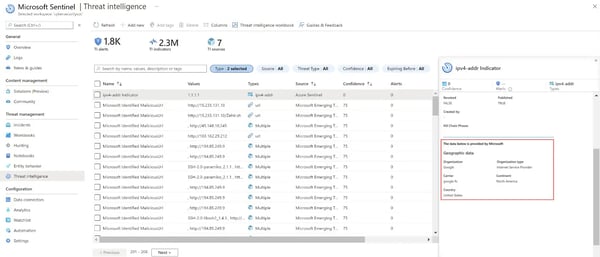
Other benefits typically include the enrichment of imported threat intelligence indicators with location and “whois” information that is displayed with the other indicator details.
Threat Intelligence also provides a useful context within Microsoft Sentinel for the deployment of Advanced Threat Hunting and Notebooks. For example, Jupyter Notebooks are often used in Microsoft Sentinel for Advanced Threat Hunting applications.
Sentinel can also Streamlines investigations with incident insights and visualizations of the full scope of an attack enabling more efficient investigation of related alerts and the review of related historical information.
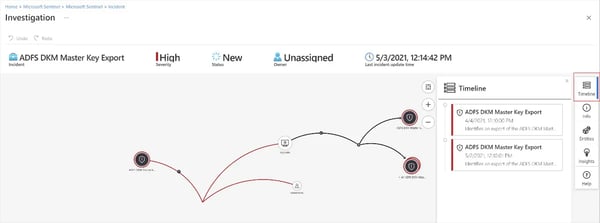
Figure 17, below, is an example of an incident investigation with Sentinel in a link analysis format.
Security Co-Pilot
Microsoft recently debuted Security Co-pilot based on OpenAI technology to assist security teams in synthesizing data from multiple sources into clear, actionable insights and responding to incidents in minutes instead of hours or days. This can help organizations discover previously unknown threats, triage signals quickly, determine threats earlier than before, and obtain predictive remediation to help stop lateral movement during an attack.
Co-pilot also assists organizations in addressing the talent gap with the demand for skilled defenders vastly exceeding the current supply. This can help security professionals make the most impact and build their skills with step-by-step instructions to mitigate risks.
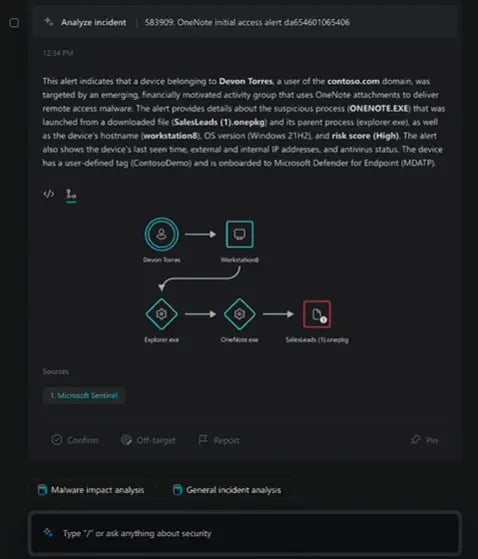
Figure 18 shows a Co-Pilot incident output with a link analysis.
Cyber Threat Intelligence Collaboration
The holistic Threat Intelligence Program is achieved with the integration of data from numerous sources, platforms, tools, services, and feeds.
It is wise for any organization to become familiar with and gain membership in the Information Sharing and Analysis Center (ISAC) applicable to their sector. For example, Defense Industrial Base (DIB) related organizations should consider the National Defense ISAC, and U.S. State and Local government entities should consider the Multi-State ISAC.
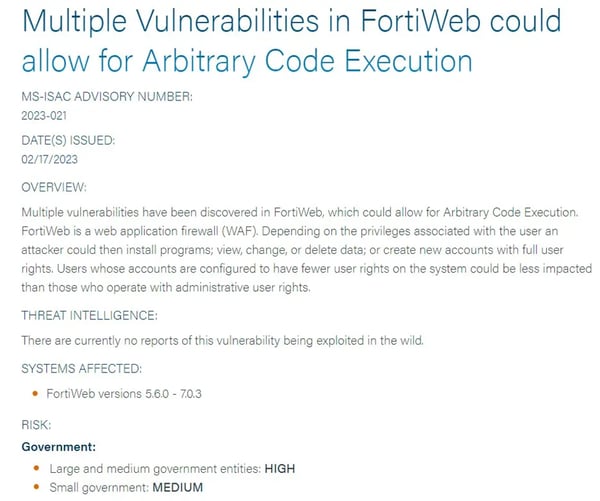
The benefits of taking part in an ISAC are vital intelligence sharing and collaboration as well as gaining experience-based lessons learned and best cybersecurity practices across a specific industry (see Figure 19 for an MS-ISAC Advisory Sample).
Other commercial, open source and government sources may be imperative for the success of the Threat Intelligence Program so do not be afraid to branch out and bring in outside relevant sources and engage in collaboration outside the conventional regime.
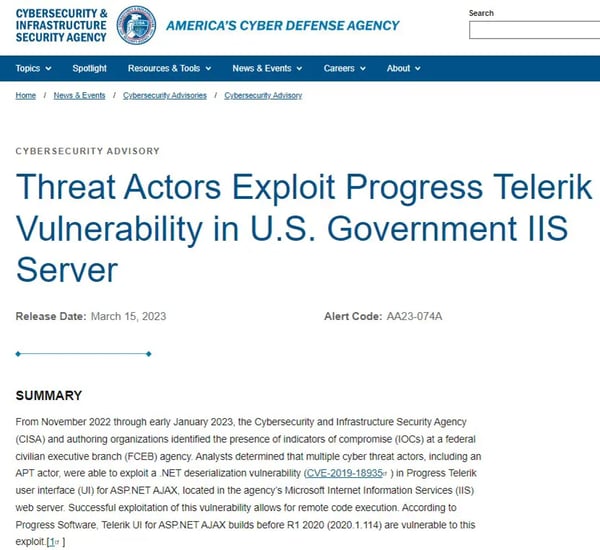
Figure 20 is an example of a government advisory from CISA on an ISS Server Vulnerability Exploit. The advisory details the threat indicators, techniques, and tools used by threat actors for cyber defender awareness
Putting it All Together
The Microsoft Threat Intelligence Stack provides a solid foundation to build a Threat Intelligence Program. Integrating this with the internal security tools, niche intelligence sources, collaboration with industry threat intelligence sharing groups, the appropriate alignment of the organization’s risk needs, and associated Intelligence Information Requirements puts your overall security program on good footing toward improving the overall security posture of your organization and beyond.
References
- Alexroland. (2022, October 14). What is Microsoft Defender Threat Intelligence (Defender TI)? Microsoft Learn. https://learn.microsoft.com/en-us/defender/threat-intelligence/what-is-microsoft-defender-threat-intelligence-defender-ti
- Danielledennis. (2023, April 17). Overview. Microsoft Learn. https://learn.microsoft.com/en-us/azure/external-attack-surface-management/
- Diannegali. (2023, March 8). What is Microsoft 365 Defender? Microsoft Learn. https://learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender?view=o365-worldwide
- Dos and Don’ts for Charting Your Security Intelligence Journey | Recorded Future. (n.d.). https://www.recordedfuture.com/threat-intelligence-journey/
- Inc, R. F. (n.d.). Request a Demo of Recorded Future Cyber. https://go.recordedfuture.com/mssp-demo
- Microsoft Security Copilot | Microsoft Security. (n.d.). https://www.microsoft.com/en-us/security/business/ai-machine-learning/microsoft-security-copilot
- Moudy, S.D. (2023, March 28). Microsoft Threat Intelligence Stack. Quzara LLC.
- Mrbullwinkle. (2023, March 21). How to work with the ChatGPT and GPT-4 models (preview) - Azure OpenAI Service. Microsoft Learn. https://learn.microsoft.com/en-u/azure/cognitive-services/openai/how-to/chatgpt?pivots=programming-language-chat-completions
- Multiple Vulnerabilities in FortiWeb could allow for Arbitrary Code Execution. (n.d.). CIS. https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-fortiweb-could-allow-for-arbitrary-code-execution_2023-021
- Threat Actors Exploit Progress Telerik Vulnerability in U.S. Government IIS Server | CISA. (2023, March 15). Cybersecurity and Infrastructure Security Agency CISA. https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-074a
- Urquiza, N. (n.d.). Cyber Threat Intelligence (CTI) Program. https://thinkinginsoftware.blogspot.com/2019/02/does-your-organization-and-all-your.html
- Yelevin. (2023, March 14). What is Microsoft Sentinel? Microsoft Learn. https://learn.microsoft.com/en-us/azure/sentinel/overview


