Threat hunting with Microsoft Sentinel is not only powerful but is also an effective way to detect and arrest cyber threats that evade traditional security defenses. Utilizing machine learning and advanced analytics, threat hunters are able to skim through extensive amounts of data and investigate for indicators of compromise that may be an indication of an active threat. Microsoft Sentinel is a proactive approach to minimize the risk of a cyber attack that could compromise your organization’s sensitive information.
What is Kusto Query Language?
KQL (Kusto Query Language) to query and analyze data is a key feature of threat hunting within Microsoft Sentinel. Threat hunters are able to utilize the powerful and flexible language to write complex queries to withdraw insights from the data thus making the ability to identify and analyze potential threats in large, complex sets of data much quicker and easier.
KQL can be used to analyze network traffic for unusual patterns, or to search for specific file types, or IP addresses. This can help a threat hunter to detect malicious activities such as botnets, malware, and phishing attacks. Additionally, KQL can also be used to create custom notifications and alerts which can alert the threat hunter to potential threats in real time.
To demonstrate, we will review 5 advanced security cases that can be detected by using Microsoft Sentinel and KQL:
Detection of Credential Dumping:
You can search for specific process names and command line arguments to detect when an attacker is attempting to dump credentials from a system. The example below demonstrates how the following KQL query can be utilized to identify command line activities related to Mimikatz:
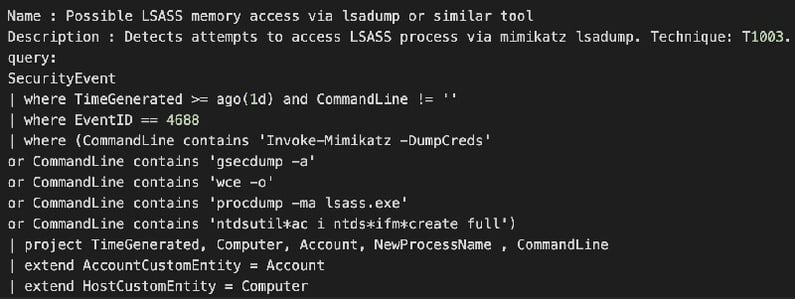
Detection of Lateral Movement:
You can identify when an attacker is trying to move laterally within your network by analyzing the network traffic and looking for non-typical patterns. The example below demonstrates how the following KQL query can be utilized to identify abnormal RDP usage:
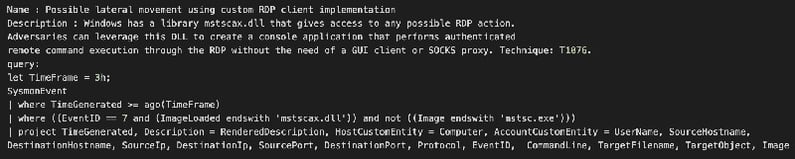
Detection of Ransomware:
You can identify when an attacker is trying to encrypt files on your network by searching for specific file extensions and file names. The example below demonstrates how the following KQL query can be used to detect files with hive.bat or shadow.bat:
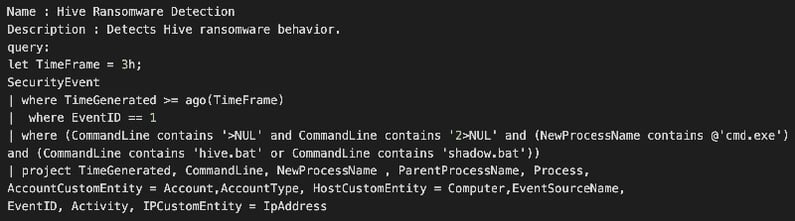
Detection of Advanced Persistent Threats (APT):
You can determine when an attacker is attempting to establish a long-term presence on your network by monitoring and analyzing behaviors of specific domains and IP addresses. The example below demonstrates how the following KQL query can be utilized to identify connections to a known APT command and control server:
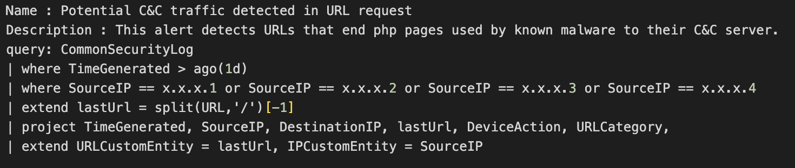
Detection of Phishing attempts:
You can determine when an attacker is attempting to Phish for sensitive information by analyzing email traffic and searching for specific keywords. The example below demonstrates how the following KQL query can be utilized to identify a newly created inbox rule that deletes emails containing certain keywords or junk emails using another set of suspicious keywords:
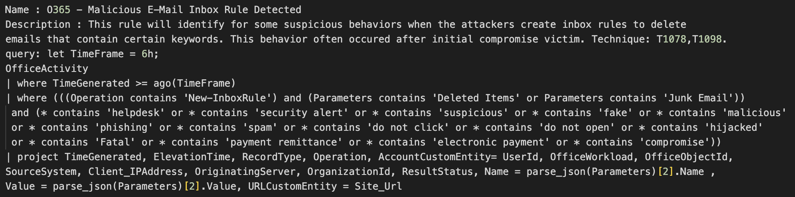
Microsoft Sentinel has a plethora of different types of queries that you can run to identify and respond to cyber threats. Utilizing advanced analytics and KQL, this powerful proactive combination within Microsoft Sentinel provides a comprehensive threat hunting solution which assists in detecting and neutralizing cyber threats. This gives threat hunters a large advantage so they can quickly respond before their organization suffers damages.
Contact us today for more information.


